What is Single Sign-On (SSO)
What is SSO? How Does Single Sign-On (SSO) Work?
SSO or Single sign-on combines several different application login screens into one. Using this technology, users only have to enter their login credentials one time on a single page to access all of their SaaS applications.
Imagine if you are in a bar and were asked to show your identification card to prove your age when you attempted to purchase additional alcoholic beverages. You would quickly become frustrated with the continual checks and might even attempt to circumvent these measures by sneaking in your beverages. However, most establishments will only check your identification once and then serve you several drinks throughout the evening. It is somewhat like an SSO system; instead of establishing your identity repeatedly, SSO will ask for credentials once to access all SaaS applications.
How Does SSO Work?
When a user signs in to an SSO service, it creates an authentication token that remembers that the user is verified. SSO, an IDM service, allows apps or third parties to confirm user identity. Identity standards allow encrypted tokens to transmit securely between the server and the apps to ensure that a user has already been authenticated and has rights to access the apps.
SSO works upon a trust relationship between the service provider and an identity provider. The trust relationship is based on a certificate exchanged between the identity provider and the service provider. Any app the user accesses will check with the single-sign-on service, and the SSO service passes the authentication token to the app, and the user is allowed in. If, however, the user has not yet signed in, SSO will keep asking to log in.
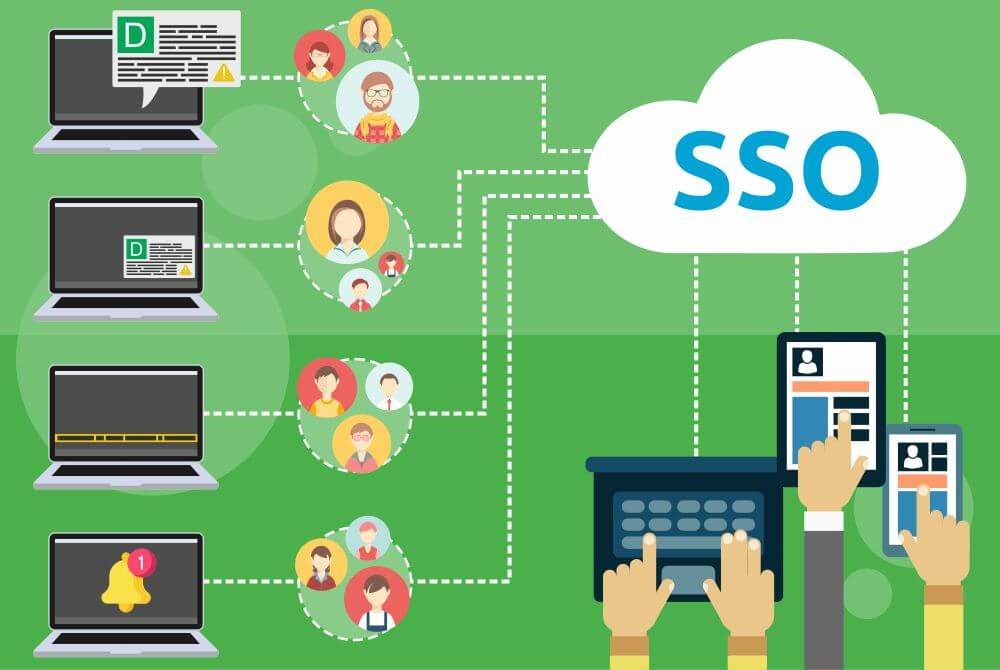
An SSO service doesn’t remember the user credentials since it does not store user identities. Most SSO services work by checking user credentials against a separate IDM service.
An SSO is a go-between that confirms whether a user’s login credentials match with their identity in the database without managing the database itself.
How Do Authentication Tokens Work?
The ability to pass the authentication token to external apps is crucial in the SSO process, and it thus enables identity verification to take place separately to make SSO work.
Think of an event where only a few people are allowed. The only way to enter the event is when the guard has checked a guest with a stamp on his hand. The event staff checks the stamps of every guest to make sure they can enter the event. However, not just any stamp will do; event staff knows the exact shape and color of the stamp used by the guards at the entrance.
Similarly, authentication tokens have their communication standards to ensure correct and legitimate. As webpages are written in HTML, authentication tokens are written in SAML (Security Assertion Markup Language).
Advantages Of SSO
Being more straightforward and more convenient for users, SSO is more secure. It may seem counterintuitive: how can single log in with one password be more secure than multiple sign-in and passwords? Here are a few of its benefits.
1. Strong Password
Single SSO requires a single password and login; it is easier for users to create, remember, and use stronger passwords. As users always use a strong password; therefore, it isn’t guessed and is random enough that a brute force attack isn’t likely to succeed.
2. No Repeated Passwords
It is difficult for users to remember passwords for several different apps and services; users will likely re-use passwords across services. Using the same password across services is a huge security risk because all services are secure, even with the weakest password protection. If the service’s password database is compromised, attackers can use the password to hack all users’ sensitive data. Therefore, SSO eliminates this scenario by reducing all logins to one login.
3. Better Password Policy Enforcement
With one password entry, SSO provides a way for IT teams to enforce password security rules. Companies require users to reset their passwords periodically. With SSO, password resets are easier to implement: instead of constant password resets across different apps and services.
4. Multi-Factor Authentication
MFA uses more than one identity factor to authenticate a user. In addition to entering a username and password, users might also have to use a code that appears on their smartphone. Possession of this physical object is a second “factor” that establishes the user is who they say they are. MFA is more secure than relying on a password alone. SSO activates MFA at a single point instead of having to activate it for several dozen apps, which may not be feasible.
5. Single Point For Enforcing Password re-entry
To ensure that the same user is still active on the signed-in device, administrators can require re-entering credentials after a particular length of time. SSO allows them to accomplish this from a single location for all internal apps, rather than enforcing it across various apps, some of which may not support it.
6. Internal credential management instead of external storage
User credentials are typically held remotely, unmanaged, by programs and services that may or may not adhere to standard security practices. On the other hand, SSO stores them inside in an environment where an IT team has more control.
7. Less time wasted on password recovery
In addition to the security benefits, SSO enables internal teams save time. Users spend less time login into numerous apps to conduct their work, while IT spends less time helping users recover or reset their passwords for dozens of apps. It has the potential to boost productivity in the workplace.
With 15 years of experience and security solution management veterans, LTS Secure management controls and secures user access to applications and websites; it can act as a replacement for most VPNs. LTS Secure integrates with SSO providers to identify users and enforce their assigned access permissions.
Connect to Consult with LTS Secure Team to explore how Single Sign-On (SSO) product provides enterprise an easy and seamless access to all resources with one set of credentials providing to any type of devices or applications.