Overview
What is User Entity Behavior Analytics (UEBA)?
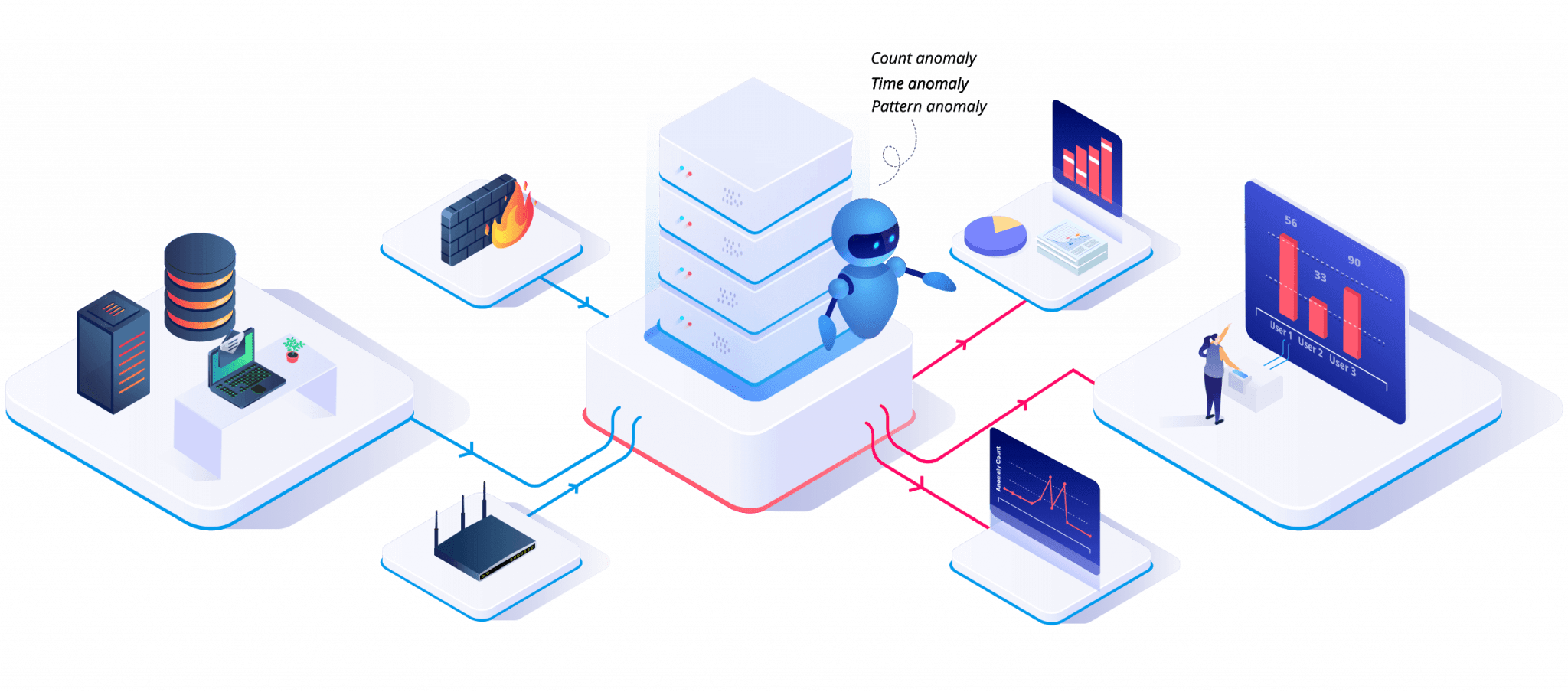
Why Would an Organization Need UEBA?
How Does UEBA Work?
The UEBA Solution Has Three Main Components
Benefits of UEBA
Some Essential Benefits of UEBA and Why Enterprises Should Consider Adopting It
Requires Fewer IT Analysts
As with all corporate software that leverages gadget learning and synthetic intelligence, software programs replace the time and effort of employees who might typically be doing the process. This prospect may excite many organizations, while IT experts would possibly drawback; however, the development of UEBA answers will not result in a dramatic headcount discount.
Suppose a company requires fewer IT Syslog analysts once the UEBA system is on autopilot. In that case, it can divert those staff members to other higher-value projects that might be more mission-critical.
Larger businesses with complicated safety necessities, including multinational corporations and governments, understand the need for additional IT staff and protection analysts to set up, configure, and manage the machine and communicate regularly with employees.
Moreover, suppose the agency decides against incorporating automatic reaction competencies, which prefer to analyze the uncommon behavior earlier than taking motion as an alternative. In that case, you will dispatch additional safety analysts to the worker or hardware place.
Reduced Costs
Risk Mitigation
Key Features
Data
Integration
Easily compile data from event logs, deep packet inspection, and outside threat intelligence, attribute behaviors, and create a master database containing all communications within the network to establish a baseline. Use this baseline to later pinpoint deviations indicating malicious intent.
ML Enabled
Analytics
With Machine learning abilities to enable user and entity behavior modeling and analytics based on various organizational components. With real-time security events and ML, we can detect and prevent threats that traditional tools miss.
Reduce False
Positives
Building profiles for each entity, UEBA uses context surrounding behaviors to differentiate between attacks and false positives.
Key Benefits
Detection of Hijacked Accounts
Attackers who steal valid user credentials behave differently than real users. UEBA uses real-time detection to ascertain if something is out of the norm and responds to the threat through various real-time responses such as Block, Modify, Re-authenticate or Multi-factor authentication. This ensures that the real threats are addressed before they try to harm the system.
Reduced Attack Surface
UEBA sends insights to the users and the security teams through interactive analytics, which allows them to know about the loopholes or weak points before an incident happens. These insights help reduce the attack surface, which makes it difficult for the cyber attacker to breach the network.
Privilege Abuse and Misuse
In any organization, privileged users have extensive access to the system, data, and applications, which is why they pose a higher risk to the organization. UEBA’s algorithms ensure that access rights are used appropriately and give an overview of what kind of privileges individual users should have.
Improved Operational Efficiency
It takes a lot of effort to identify threats manually through alerts. UEBA can manually identify and validate threats without manual intervention through automation and security intelligence. This level of automation allows security to focus on real threats rather than alert chasing.
Data Exfiltration Detection
UEBA analytics help detect potential data exfiltration before it happens, thus allowing businesses time to prepare a strategic plan to prevent data theft. It can even help identify Advanced Persistent Threats (APT). UEBA has proven itself to be an indispensable asset in the world of cyber security. According to experts, user and entity behavior analytics is a better model for attack detection, and they maintain that it is going to enable more accurate detection of cyber attackers threatening networks.
Resources
Explore valuable cybersecurity resources
Let's Connect Now !
