SEM, which stands for safety event management, is much like SIM, even though instead of focusing on historic log facts, it attempts to work in actual time, or as near it as viable, to pick out particular events relevant to protection experts. For example, if someone in your network manages to elevate their privileges to admin fame in a manner that is out of the ordinary, an SEM machine must let you understand it.
SIEM Solution Architecture Implemented in Cybersecurity
LTS Secure SIEM Tools
Enable detection, prevention
and remediation of advanced threats.
SIEM
Combining Security Information Management (SIM) and Security Event Management (SEM), Security Information and Event Management (SIEM) provide real-time tracking and evaluation of occasions as well as monitoring and logging of safety information for compliance or auditing purposes. SIEM Security was created from various extraordinary tracking and evaluation additives. The rise in cyberattacks and the tighter protection regulations required by groups make SIEM a preferred approach. This is being followed by more and more businesses.
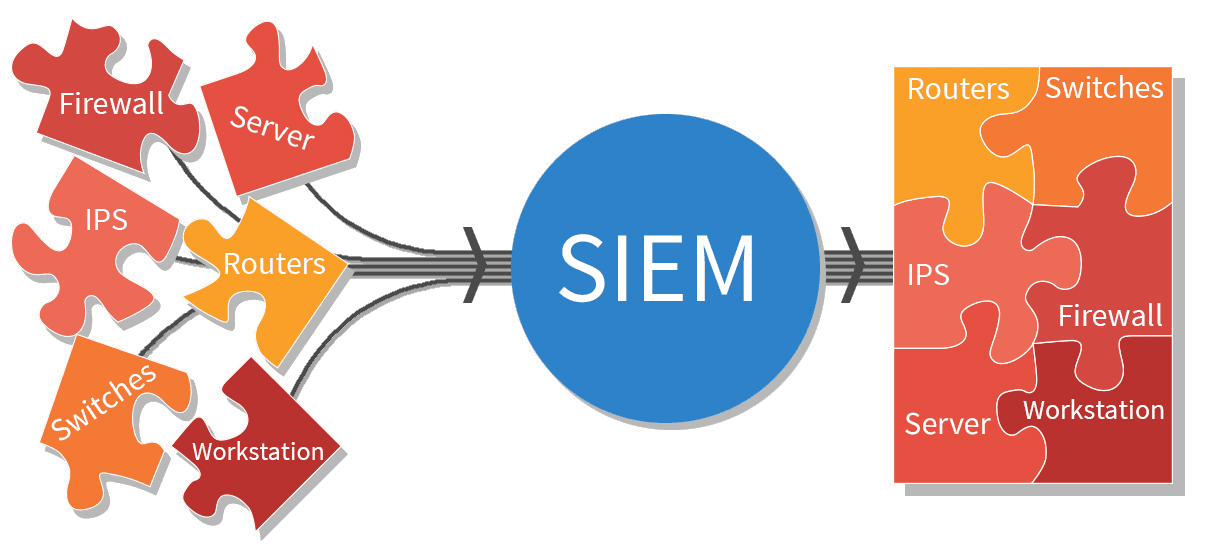
What is SIEM Security?
SIEM is a safety answer that facilitates the employer’s ability to recognize capacity security threats and vulnerabilities before they pose a danger of disrupting the commercial enterprise operation. It surfaces user behavior anomalies and uses artificial intelligence to automate many guide methods associated with threat detection and incident reaction.
It has become a staple in cutting-edge-day safety operation facilities (SOC in Cyber Security) for security and compliance management use cases. Over the years, SIEM has matured to be greater than the log management tools that preceded it.
Today, SIEM gives advanced customers and entities the ability to conduct analytics (UEBA) thanks to the electricity of AI and system mastering. Its miles are a reasonably efficient information orchestration device for dealing with ever-evolving threats, regulatory compliance, and reporting.
The SIEM Solution permits enterprises to effectively acquire and examine log data from all digital belongings in a single location.
SIM vs. SIEM
SIM, which stands for safety facts management, is a device that provides evaluation and reporting for ancient safety activities—with historic here meaning not that these activities are part of a few epic, crucial ancient occasions, but simply that they came about in the beyond. SIM structures grew out of the log control field and paintings to automate the collection of log records from various security gear and gadgets and surface those statistics to security managers.
Know the SEM Definition
A SIEM system is simply a device that mixes the capabilities of SIM and SEM software. It’s quite rare at this point to find software that offers only SIM or SEM software. It is rare to discover a software program with the most effective SIM or SEM capability.
How Does SIEM Works?
You must have expert logs and other built-in features from all your safety gadgets built into the SIEM platform.
Built-in integrated SIEM sellers will accomplish this: Packages built on various systems have the competencies to export log statistics to a primary server, and your SIEM platform can import them from there.
Built-in integrated SIEM sellers will accomplish this: Packages built on various systems have the competencies to export log statistics to a primary server, and your SIEM platform can import them from there.
The amount of information transmitted and processing electricity necessary at the endpoints can degrade the overall performance of your structures or community if you don’t implement them carefully.
SIEM marketers can relieve a few burdens by routinely parsing out some records even before sending them over to the community.
SIEM marketers can relieve a few burdens by routinely parsing out some records even before sending them over to the community.
Know the UEBA Solution
UEBA Solution is a category of security solution that incorporates innovative analytics technology, including machine learning, to find abnormal and risky behavior by users, machines, and other entities on the corporate network, often in conjunction with Security Incident and Event Management solutions.
Cyber Security Solution
Cyber security solutions are technological tools and offerings that help defend corporations against cyber-assaults that may bring about application downtime, theft of touchy statistics, harm to reputation, compliance fines, and other destructive outcomes.
Know SIEM Working Facts
Manifestly, the amount of information generated via this SIEM instrumentation is large. The number one value introduced by SIEM suits is that they observe facts analysis to ensure that the handiest profitable operations get added for your safety operation middle.
AI and ML Use in SIEM
These systems use correlation engines to try to join disparate log entries or other alerts that don't appear worrisome on their own; however, taken together, they can spell hassle. Those engines blended with particular artificial intelligence and machine-learning strategies used to smell out assaults are what diverse SIEM carriers use to differentiate their services from one another.
How SIEM Software Use in IT Industry?
SIEM software improves an IT environment's security cognizance by combining protection information management (SIM) and security occasion management. LTS Secure is the call for all your protection options to safeguard your organization from any disruption from cyber-attacks.
Dashboards
Collect and distribute information like MTTD and MTTR, account activity, suspicious users, terminated accounts, etc., in a meaningful way, depicting trends and patterns in easily downloadable formats to simplify and support security-related decisions and organizational goals.
LTS Secure SIEM Benefits
Empowering organizations with LTS Secure NXT-GEN SIEM with XDR and UEBA benefits from Flexible Integration to Augment your Security stack.
Understanding Threats
Monitor logs efficiently and report suspicious events from the vast amount of data generated and collected from various business processes.
Correlate Data
Collect, normalize, and analyze logs and ingest threat intelligence feeds directly to understand real indicators of compromise (IOC) to further safeguard the network.
Present Data
Present Data With customizable reports, present data in different ways to spot trends, patterns, anomalies, etc. and increase visibility and transparency within the network.
Compliance Guideline
Adhere to various compliance legislations like GDPR, CCPA, HIPAA, PCI-DSS, etc. through custom SIEM reporting and safeguard data as well as organizations.
Stay a step ahead of the latest and most sophisticated threats.
Resources
Explore valuable cybersecurity resources
Let's Connect Now !
