Get to Know More About LogRhythm UEBA
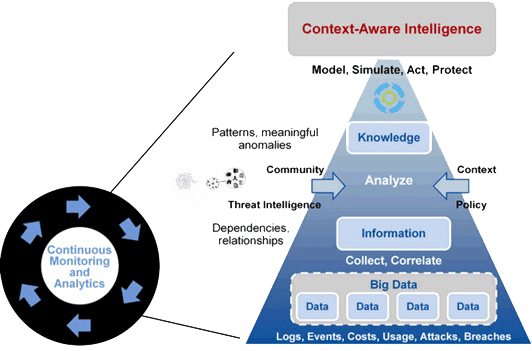
The cyber danger landscape has become more sophisticated due to the extent and complexity of assaults for LogRhythm UEBA. That is why it’s miles more difficult than ever to detect anomalous personnel behaviour or compromised account.
Log Rhythm is familiar with the preference for extra visibility and superior analytics to discover anomalies tied to capacity consumer assaults. That’s the muse of Log Rhythm UEBA, our cloud-native person entity UEBA Solution.
Why Is It Necessary to Have Log Rhythm UEBA?
Whenever you want to evaluate a hobby in opposition to a user’s baseline, superior analytics come into play. Formerly referred to as CloudAI, Log Rhythm UEBA is straightforward to install within the Log Rhythm SIEM platform. It uses gadgets to gain knowledge to come across outliers like what’s normal conduct as opposed to atypical behaviour that warrants additional research.
Most of the time, security groups require to gather and analyze a lot of data manually to try to identify anomalies that are potential threats. Log Rhythm UEBA saves analysts time by prioritizing only threats or anomalies that require further investigation.
How Log Rhythm UEBA adds A Greater Value –
Whilst trying to perceive anomalies for your community, detection is critical. LogRhythm UEBA adds additional layers of detection against individual-based threats and different difficult-to-find anomalies that would otherwise move left out.
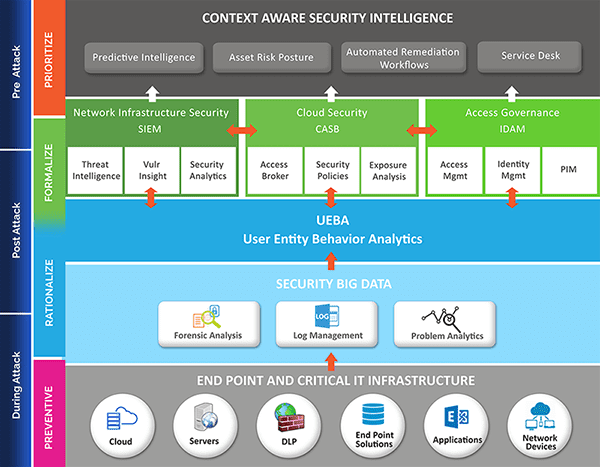
Every other benefit of LogRhythm UEBA is that it functions as a sophisticated UEBA log source in the SIEM and smoothly integrates with the LogRhythm UEBA, connects without delay to the data indexer (DX) to acquire the log it calls for. Log Rhythm UEBA’s native integration offers analysis more context and visibility to find anomalies.
SIEM security solutions permit enterprises to understand the capability threats and vulnerabilities before they risk disrupting the commercial enterprise operation.
It surfaces person conduct anomalies and uses artificial intelligence to automate many manual processes associated with danger detection and incident response. It has become vital inside the advanced day protection operation middle (SOC) for safety and compliance management use instances.
LTS Secure’s advanced cyber security solutions s an adequate exercise, with advanced technologies and know-how that will help your agency to defend against those cyber-assaults, safeguard your commercial enterprise-essential application and statistics, and help accelerate recovery from an information breach or similar disruption.
LTS secure cyber security offerings help defend platform configuration and application information using tight safety, immutable garage, and anomaly detection even as orchestrating speedy and dependable recuperation on the catastrophe recuperation.
SOAR Solution permits the group to gather valuable security data, identify and examine, and cope with current and capability threats and vulnerabilities from different sources.
As a cloud-native upload on LogRhythm, UEBA functions as a complicated UEBA log supply in the log rhythm SIEM platform. You could create a customizable dashboard, run and keep searches, and leverage AI Engine policies to set alarms.
Get Geared Up to Defend With LogRhythm UEBA
- Resolve the prevailing and the destiny’s threats, too- With a cloud-local architecture, enhancement is delivered right now. The group can be superior and organized to solve now not simply these days’ hazards, but also the inevitable superior chance that can interfere to your way.
- Get Smarter and faster: LogRhythm UEBA learns from and evolves for your environment. It uses system mastering for continuous, automated turning without guide intervention, so the security grows plenty more brilliant.
- Leave information practice: Log Rhythm helps customers prepare and analyzes metadata using Log Rhythm’s device facts Intelligence (MDI) cloth. The MDI framework affords statistics enrichment and normalization with specific, rich metadata and contextual facts that feeds into the LogRhythm SIEM Platform into LogRhythm UEBA.
- Reap speedy time to price – start benefitting without delay with cloud delivery. Plug-and-play implementation lets your group know their venture prefers spending precious time imposing and retaining a brand new tool.
- Accelerate hazard detection: As an integrated add-on for the Log Rhythm SIEM Platform, Log Rhythm UEBA gives your group extraordinary detection by using gadgets getting to know to locate tough-to-locate anomalies.
What’s New in Log Rhythm UEBA?
At Log Rhythm, it’s far constantly innovating and updating its product. That’s a part of the continued dedication to every purchaser.
The new Log Rhythm version is added, which can assist the group in hitting upon better and alerting less to reduce alert fatigue. The new models include new IDs and unbelievable tours among starting place locations.
SIEM is a warning statement machine that centralizes security alerts from more than one resource for overview and action and generates compliance reviews.
SIEM answers use information aggregation and statistics normalization to provide a consolidated view of all protection events on a single platform
Safety statistics and occasion management is a risk detection device that centralizes safety signals from numerous assets for overview and action and creates compliance reviews.
SIEM solutions use records aggregation and facts normalization to provide an integrated view of all protection occasions in a single platform.
To Know More Details about LogRhythm ,visit https://en.wikipedia.org/wiki/LogRhythm.
What are the top 10 cyber security threats from your perspective?
Cyber-attacks have several negatives. Whilst an assault is accomplished, it may cause statistics breaches, ensuing in statistics loss and records manipulation. Companies incur monetary losses, clients’ considerations get hampered, and severe reputational damage. Cyber protection is a procedure of protecting networks and computer systems and their issue from unauthorized digital access. LTS affords a pleasant cyber protection answer for your employer.
The top 10 forms of cyber-assaults are –
Malware assault – This is the most not unusual sort of cyber assault. Malware refers to malicious software program viruses, worms, adware, ransomware, and Trojan.
Phishing assault– it’s far a sort of social engineering assault wherein attackers impersonate to be a relied on contact and send the victim fake emails.
Password Attack– in this attack, the hackers crack your password with numerous packages and password-cracking gear.
Man-in-the-center– Attack–is also called an eavesdropping attack. On this, an attacker intervenes in a two-component conversation. The attacker hijacks the consultation between a purchaser and a number.
SQL. Injection attack – A based query Language (square) injection assault occurs on a database-driven website whilst the hacker manipulates a general square query.
Denial-of-service attack: A Denial of provider assault is a significant danger to agencies. Attackers goal the device server or networks and flood them with visitors to exhaust their resources and bandwidth.
Insider danger: An insider threat no longer contains a third birthday party but an insider.
Cryptojacking: The word Cryptojacking is nearly related to cryptocurrency. Cryptojacking takes vicinity when an attacker access a person else pc for mining crypto foreign money.
Zero-Day makes the most – Zero-day exploit occurs after the announcement of a community vulnerability; there is no answer for the vulnerability in maximum cases.
Watering hole assault: The victim here is a selected employer of a business enterprise, area, and so on. In such an attack, the attacker objectives websites that the targeted institution may often utilize. Websites are recognized each by closely tracking the organization and using guessing.
Top 5 Things to Consider When Replacing Traditional SIEM Security
Identifying new security information and event management (SIEM) capabilities supports your organization’s business and security goals and successfully plans, designs, and deploys new, integrated, analytics-driven SIEM tools that meet your requirements. It is important. know more What is SIEM Security and Why it is Important.
Suppose you’re considering replacing traditional security information and event management (SIEM) technology. In that case, you might say: Ensuring that SIEM security is doing its job is more important than ever, and the potential for the latest SIEM is more significant than ever. Since the introduction of SIEM technology on the market, the underlying technology has grown significantly. If you’re running a traditional SIEM, you can’t expect to withstand the frequency and sophistication of today’s cyber-attacks, mainly due to the rapid pace of digital transformation and migration to the cloud.
When ready to replace your old CIM, consider new features important to your organization’s business and security goals. You need to plan and design for a successful transition to analytics-driven Security tools, given the resources you need and the potential challenges your organization faces to get up and to run and troubleshoot. If you are considering and planning to replace your old CIM, here are the top five things to consider when replacing your old CIM:
1. Business driver
2. Required skills
3. People and processes
4. Planning and design: How to achieve it
5. Mission

Business Driver –
Data security driven by digital transformation and migration to the cloud will be a top priority for businesses, and next-generation computer security solutions and technology will help. Data security driven by digital transformation and migration to the cloud will be a top priority for businesses, and next-generation SIEM technology will allow it. More and more companies are moving to the cloud rapidly, and new cloud infrastructures require sophisticated cloud strategies that you can implement quickly. Unfortunately (sometimes tragically), security requirements are often overlooked due to the technical challenges and time constraints of cloud migration.
Security professionals must analyze real-time security data to respond to increasingly sophisticated and complex attacks and breaches. You can start your cloud migration seamlessly and securely with a robust new SIM solution. Find out-of-the-box cloud security monitoring content that facilitates threat detection and response across hybrid, cloud, and multi-cloud environments. You also need to include cloud attack detection rules and various cloud attacks.
Required Skills –
One of the problems with traditional SIEM is that it reduces the effectiveness of the entire Security Operations Center (SOC). Instead of issuing accurate, prioritized, and meaningful alerts, the IT team becomes full of noise, leading to alert fatigue. This is a state where everything looks like a priority and cannot be prioritized.
The right SIEM solution should be based on your business needs and whether you need an on-premises, cloud, or hybrid solution. There may be specific needs for threat intelligence, database or application monitoring, industry-specific content, and compliance reporting. Threat detection rules are also worth considering, depending on how often the rules are updated and how easy it is to customize. Companies with old operational capabilities can use security orchestration, automation and response (SOAR) capabilities and analytics, forensic / hunting, and the native endpoint, network, user, and entity behavioral analysis (UEBA) modules. Report/compliance is available.
People and Processes –
Replacing traditional SIEM represents a new challenge and a new opportunity for the team. If you need additional training, you can do it at the right time when the new SIEM is being built, and this gives the team complete control when the new SIEM is up and running.
In addition to your staff, consider the level of external and external support you may need from planning, product, and implementation perspective. Depending on your schedule and budget, building professional service infrastructure components and using in-house architecture and engineering can be more cost-effective than conducting parallel on-site training for new SIEM tools.
This is also the best time to evaluate the process. The tool of your choice may require you to redefine some of the processes involved in alerting, incident management, and drill-down analysis. You may also need to coordinate operations across vendors, not just the architecture and cloud implementation teams. Changing the process can be difficult, but the benefits are enormous. Risk-based alerts allow teams to focus on real threats and other essential tasks with fewer alerts and false positives. Also, with traditional SIEM, finding a way to optimize storage and keep your environment running at full functionality is time-consuming and resource-intensive. Replacing legacy SIEM in the cloud eliminates the need to manage your on-premises infrastructure and acts as computer security.
Planning and Design: How to Achieve It
Consider scalability and integration when evaluating and planning a new SIEM. Consider how much data you need each day and how many sources of data you have. Integration can be a significant challenge for companies’ SIEM deployments. Therefore, consider other technologies that need to be integrated with new SIEM technologies, such as user authentication.
§ Enterprise Resource Planning (ERP) solutions, third-party vendors, big data platforms, or SOAR
§existing ticket and event management systems
§ Data Streaming Security Technologies
Finally, think about the cloud. Experts recommend designing SIEM to automate data ingestion between on-premises and cloud data sources as much as possible.
Mission
Most enterprise organizations face integration challenges when migrating to a new SIEM. When deploying a new system, you need to keep your existing system online, as you need to manage both SIMs for a seamless migration. Migration may require integrating multiple security technologies, the transformation of rule and use case migrations, and streaming data from parallel deployments (such as enterprise Syslog). The goal should be an invisible transition, a transition that does not risk visibility or detection.
Many of the new SIMS are customizable and automated when it comes to deployment options.
Organizations can combine tools, virtual appliances, and software to create feature stacks for flexible deployment and horizontal scalability. The new SIEM also allows you to customize existing rules and predefined reports. The new SIEM can also combine on-premises, cloud, and hybrid deployments to create cloud-based SIEM solutions beyond detection and feedback.
The Maximum SOAR Solution includes a playbook that provides best practices and procedural instructions. Playbooks ensure consistency, compliance, and faster and more reliable incident identification and remediation.
UEBA brings modern machine learning (ML) analytics to the security world. You can easily detect strange patterns of user behavior. Abnormal activity and potentially malicious actors are detected when the system is trained to recognize standard and typical usage patterns. UEBA Products can be seen as the latest evolution of traditional intrusion prevention and detection systems.
For more details about SIEM, visit https://en.wikipedia.org/wiki/Security_information_and_event_management.
Splunk is a technology used to search, monitor, visualize, and analyze machine data in real-time. This is a log management and analysis tool. Most people ask a frequently asked question: Is Splunk SIEM? Splunk is not SIEM, but it can be used for similar purposes. It is primarily used for log management and stores real-time data as events in the form of indexers. Useful for visualizing data in the form of dashboards
SIEM (Security Information and Event Management) is a security and monitoring system consisting of various monitoring and analysis components. The recent rise in cyber-attacks, coupled with the tightening of security regulations required by organizations, has made SIEM the standard security approach adopted by more and more organizations.
Validating Access rights within systems from LTS Secure
A key component of IT infrastructure that controls, manages and audits the security framework, IT control provides central visibility and compliance on various roles with the security architecture. Not only does it improve audit processes, it also automates and simplifies revalidating an account, allows approving roles, accounts and groups for specialized users within a single activity. Access Recertification ensures that organizations internal policies and compliance regulations are being adhered by auditing users’ access privileges
Our solution helps organizations mitigate access risks, reduce review time and enables you to act immediately to correct any unwanted or unauthorized permissions, preventing unwarranted access.
With major benefits, LTS Secure Access Recertification;
- Allows IT & Security teams to ensure that resources that were assigned to user’s, were only had the required permissions for the correct period of time.
- Helps comply with compliance requirements like PCI-DSS and ISO 27001.
- Significant reduction in costs due to potential security incident been avoided.
Incorporating a wide array of features, LTS Secure user access privileges lets business control and audit seamlessly answering questions regarding access, approvals and policies. This automated alternative ensures high productivity at lesser costs and additionally higher ROI by utilizing collected information to refine the identity and access management program.Validating access rights within systems for compliance and security risk management is a comprehensive and daunting task especially when the organization is dispersed and not well equipped with security teams, services and tools. LTS Secure Security Solution allows organizations to formally validate users and accounts within systems, make them more manageable ensuring access rights are appropriate and thereby increase transparency.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
Email–enquiry@ltssecure.com
Building a productive & fully functioning SOC is crucial for every organization due to the current threat landscape. Threat actors are becoming more sophisticated by each passing day, leaving almost no trace of familiar patterns in their attacks, forcing SOC teams to use their full potential.
To do so, SOC teams need to bring efficiency into their processes, while also improving their incident response strategies, all of which are getting hampered by the sheer number of security alerts generated by their security solutions like SIEM.
Why do SOC teams need SOAR if they already have a SIEM?
For SIEMs to differentiate between normal & suspicious, it needs to be periodically upgraded & tuned, which is typically done by engineers & analysts. However, responding to a plethora of alerts triggered by a computer security still remains a manual process. For every alert generated, analysts need to review & investigate it, determining if the alert is a false positive or an actual incident that requires further investigation & remediation, which again is a manual process.
While most Security information and event management possess a wide range of capabilities, they were not created to unify technologies, processes & people within a SOC. This is exactly where a SOAR solution comes into play.
While SIEM takes care of detecting potential security incidents & generates alerts for them, SOAR takes these alerts to the next level by triaging data, responding to them & taking remediation steps where deemed necessary, thus adding significant value to the existing SIEM solution being used.
LTS Secure SOAR
LTS Secure SOAR is a perfect solution for organizations that want to streamline their security operations while increasing the overall efficiency of their SOC. The solution does this by centralizing & triaging alerts from various security solutions, automating threat analysis and repetitive tasks, saving valuable time & resources of SOC teams.
With numerous out-of-the-box connectors and easy-to-configure playbooks, LTS Secure security solution can easily be integrated with all major security solutions, providing a single centralized point of visibility with advanced case management capabilities, asset correlation view and automated response for security incidents.
Key Benefits of Using SOAR in a SOC
- Automation: By automating mundane & repetitive tasks, SOAR allows SOC teams to focus on tasks that require their
- Faster Response Time: ML Engine of SOAR enables it to identify false positives & appropriately respond to low-risk security alerts without the need for any human intervention.
- Reduced Manual Operations: End-to-End incident response helps overcome alert fatigue by automatically detecting & responding to known security threats with automated workflows.
- Improved Threat Hunting: ML Engine learns from past security incidents, enabling SOAR to evolve at the same pace as security threats, allowing SOC teams to handle threats more
- Comprehensive Integration: Supporting multiple integrations and APIs, SOAR allows multiple security products to communicate and work synchronously, increasing flexibility of organizational infrastructure using languages like Python, APIs and
- Enhanced Threat Intelligence: Provides actionable information for incident response teams by having the ability to ingest threat intelligence feeds & correlate it with security events in real
- Dashboards & Reports: Allows SOC teams, CISO’s & auditors to properly visualize & analyse relevant data, measure success & access potential business
About the Author
Diraj – Security Analyst
Diraj is a Security Analyst who has designed custom solutions for various use cases based on client requirements from different industries helping them gain better visibility.
Media Contact
Email id: enquiry@ltssecure.com Phone no: 407-965-5509
What Is SOAR and the Many Benefits That It Brings You Must Know
With the increasing number of cyber threats being faced by organizations, it has become crucial for them to effectively detect & respond to such activities before it can lead to any sort of breach. This task is further made more challenging, due to the volume of alerts being generated by various security solutions such as SIEM, UEBA, EDR, EPP, etc. Each of these generated alerts are then required to be manually reviewed, analyzed and if deemed necessary, taken action upon, causing the productivity & efficiency of an organization’s SOC to go down.
Enter SOAR
SOAR (Security Orchestration, Automation, and Response) is a security solution, enablesorganizations to collect security & threat related data from a wide variety of sources and allows them to automate response to low-level security incidents.
Orchestration – Improves efficiency when executing remediation.
Automation – Reduces time to take action (makes orchestration process more efficient). Response – Plans, manages, coordinates and monitors response to a security incident.
LTS Secure SOAR and its Benefits
Integrating our SOAR solution into your existing security stack, enables you to define, prioritize & standardize functions that respond to security incidents, thus allowing you to identify security related issues, define the solution and help automate the response, causing your overall efficiency to rise while making security more self-operating. This integration also ensures that incidents & vulnerabilities are responded to quickly, allowing security teams to better prioritize their time.
- Faster Response Time: ML Engine of SOAR enables it to identify false positives & (appropriately respond) to low-risk security alerts without the need for any human
- Reduce damage from attacks – Minimize the number of steps that actually require any sort of human intervention and help SOC teams investigate & respond quickly so they can begin the mitigation process
- Comprehensive Integration: Supporting multiple integrations and APIs, SOAR allows multiple security products to communicate and work synchronously, increasing flexibility of organizational infrastructure using languages like Python, APIs and
- Operational costs being reduced – With SOAR taking automated actions against tedious & time-consuming tasks, like responding to low-level alerts and dealing with false positives, operational costs are significantly
About the Author
Utsav – Security Analyst
Utsav is a Security Analyst who has done a number of research projects & has been involved with a number of Enterprise grade cyber security projects implementation & completion.
Media Contact
Email id: enquiry@ltssecure.com Phone no: 407-965-5509

Comprehensive cyber-security services provided through LTS Secure V-SOC BOX or various custom cyber-security measures reflecting specific business needs make an extremely cost effective way of protecting your business network and safeguarding sensitive company assets.
Providing high performance and advanced technological features, LTS Secure V-SOC BOX is a clever combination of a range of modules like AI and SOAR based SIEM, Cloud Access Security Broker (CASB), Identity Management (IDM), Security Analytics, Access Recertification and AI and SOAR based User and Entity Behaviour Analytics (UEBA) aiming to cover different layers of security.
Ensuring cost effectiveness and high performance simultaneously, LTS Secure V-SOC BOX provides comprehensive security visibility of network, users and applications safeguarding your business at various levels by identifying threats, preventing malicious attacks and provide immediate remediation to attacks and breaches.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.

With numerous benefits along with advanced features, LTS Secure V-SOC BOX is a highly feasible suite of cyber security solutions specially designed for all round network security protection and defending sensitive company assets.
Advance Threat Detection for all data, users and applications, Integrated security that includes modular network, user and application visibility from single solution, Orchestration and Automation reducing false positives with orchestration rules by ~45% and increase in automation by ~60%, Compliance reporting and gap analysis reducing audit time and audit report submissions and Asset based risk and compliance includes consolidation of threats and vulnerabilities reducing business continuity risk by ~73%. Enhanced with all these benefits, LTS Secure V-SOC BOX makes a solution suitable for all businesses security requirements providing multi-layered network security.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
UEBA to protect remote employees for analysis remote threats and vulnerabilities which can impact organization data and IP
The on-going pandemic situation has created numerous security challenges for business to safeguard network and assets with cyber-attacks constantly increasing in volume and sophistication. With this situation, arises the need to strengthen the existing security measures with advanced tools, strategies and processes to build a highly resilient environment for employees working remotely.
The deployment of User and Entity Behaviour Analytics enhances focus on user behaviour and systems identifying anomalies in normal behaviours by establishing baselines for remote working. UEBA, additionally, helps identify unknown malware threats and potential breaches providing a detailed view of vulnerabilities, identification, prevention and remediation. Our strategic UEBA solution appropriately protects businesses by accessing remote employee networks and behaviour, analysing remote threats and vulnerabilities that can substantially impact organizational data and Intellectual property.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
With cyber-attacks getting more sophisticated, targeted and polished and simultaneously increasing in volume; businesses are struggling to elevate cyber-security measures to cope up with threats and malicious attacks. Managed Detection and Response (MDR) is one of the cyber-security aspects that have proven highly important in this vulnerable pandemic situation.
Raising cyber-security maturity levels, MDR helps with fail proof detection of breaches in the infrastructure as compared to conventional MSSPs. With combination of Artificial Intelligence (AI) and Machine Learning (ML), our MDR solutions strategically provide faster investigation, response and automatically contain and remediate threats posed to business networks, which is extremely important for businesses of any size during this critical pandemic situation.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.

Compelling employees to work from home, this critical pandemic situation has left business networks vulnerable to more cyber-attacks than ever. With lack of control over employee network and security practices, businesses need to overcome multitude of challenges faced by phishing emails, manipulative VPNs, files and data sharing, WiFi security and more.
With cyber-attacks becoming more sophisticated and complex, the need to implement SIEM in the business network is of utmost importance. Advanced SIEM modules for data aggregation collect data to identify and prevent malicious attacks, log management collects log data from multiple endpoints with subsequent mitigation, Security Event Correlation allows log data analysis across network applications, systems, and devices and Threat Intelligence provides safety of all organizational assets.
Providing information on potential cyber-attacks and risks, SIEM implementation and tweaking according to the changing requirements overcomes challenges specific to the Covid-19 pandemic situation and helps safeguard businesses.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.

During this critical situation of the pandemic, businesses need to be more vigilant and prepared with rampantly increasing cyber-attacks and threats to infrastructure and critical assets. With Cloud Access Security Broker (CASB) increase visibility, compliance, data security and threat protection, controlling access points for cloud infrastructure, policy enforcement in real time and identifying risks and abnormal behaviour.
LTS Secure CASB suite provides multiple functions including data loss prevention that ensures classifying sensitive data across multiple devices and files , file-level encryption that encrypts and secures data before storing it on the cloud, two factor authentication enhances user identification security, single sign-on enabling user authorization and granting access to multiple applications, access control allowing administrator to revoke access to specific devices, files or users, auditing and enforcement allowing administrators to monitor activity across the network and identify anomalies.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
Know Strengthening partners and customers businesses

Strengthening Partners and Customers’ Businesses!
With most employees working from home during this pandemic, business networks are being accessed through multiple non-secure employee networks, increasing vulnerabilities. With high prevalence of malicious attacks and threats, cyber security is currently of utmost importance to every business.
Thank you Mr. Kaushik for your valuable feedback
“With attacks and threats rising, LTS Secure monitored our VPN/Firewall activities during the lockdown period, identifying and remediating threats/risks in our environment. It gave us enhanced visibility minimizing impact on Business Continuity.
We are happy with the services and appreciate the support they have delivered during this period. Thanks LTS Secure Team! “
Lalit Kaushik
JBM Group
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.

A centralised repository for all threat indicators pulled from various providers, Threat intelligence hub provides SOC with critical IOC’s for better threat detection & response like C&C IP Addresses, URL, URI, domains, hostnames, malware hashes (MD5, SHA1, SHA256, etc.), CVE Number and Email Addresses.
Among obvious benefits, LTS Secure V-SOC BOX allows the security team to be more up-to-date with current threat landscape, methods being utilized, vulnerabilities being exploited and systems & applications being targeted. This advanced feature also conducts in-depth threat analysis and proactively identifies and prevents breaches and keeps decision makers and stakeholders informed about the latest threats and its impact on business operations.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.

While automating certain time consuming actions performed on alarms, Alarm Orchestration allows users to focus on tasks that need their attention and let LTS Secure V-SOC BOX handle repetitive actions on alarms, saving valuable time for security analysis.
Based on different conditions, Alarm Orchestration performs appropriate actions on alarmsand drastically reduces the number of false positives allowing SIEM to take actions automatically without any manual intervention and more importantly, alerting relevant stakeholders about any suspicious activity.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
LTS Secure V-SOC BOX version 5.0 features an advanced Compliance Mapping and Reporting module that allows the admin to dynamically add and deduct any number of policies as required. Defining many types of policies, this feature generates compliance reports like HIPPA, ISO 27001, PCI DSS etcetera. While previous versions only statically displayed policies, this version presents dynamically working policies.
Another important advancement in the updated version involves merging multiple compliance databases into a single database wherein data is fetched based on its ID. This creates a more convenient and simpler structure reflecting smoothly on the User Interface and User Experience.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.

Newly added plugins of LTS Secure V-SOC BOX version 5.0 – AWS & Office 365 plugins, provide threat monitoring and Privileged Activity Monitoring for AWS and Office 365. While UEBA fetches data from these plugins and enhances alarm context, SIEM receives the enhanced version and monitors alarms for security analytics.
Monitoring suspicious events and threats, this feature has numerous benefits allowing appropriate rule creation like correlation and cross-correlation rules, identifying threats and potential attacks in-progress and more. Synchronizing with SIEM and UEBA, we can now experience complete visibility into on-premise and cloud activities via a single console.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
Based on alarm fields like source and destination IP address, risk value, intent name etcetera, Alarm labelling provides numerous benefits like tagging labels, enhancing it to auto-labelling and involving less or zero manual efforts to reduce noise.
In version 5.0 of LTS Secure V-SOC BOX, the Alarm labelling feature allows automatic label tags to duplicate alarms after the initial tag; which means you don’t have to manually tag every duplicate alarm generated and will reduce noise with any manual intervention.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.

Strengthening micro, small and medium enterprises (MSME) with financial services, Veritas Finance Pvt. Ltd. serves about 48 thousand customers through 202 established branches. Our new project entails serving our client from the Finance Industry with an important cyber security aspect; Identity Access Management (IAM).
To enhance security profiles and simplify audits and reporting, with Single Sign Off (SSO) on both Web and Mobile application, Veritas Finance procured our security services to strengthen multilayer network security. Implementing LTS Secure’s Identity Access Management module, focussing on asset protection, we allocated selective network access to specific personnel.
About LTS Secure:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
LTS Secure and Inventus Pune Collaboration
We are delighted to announce our partnership with Invent Onus Tech, based in Pune, India; with the collaboration we aim to provide cyber security consultation and serve the Indian market with advanced AI & ML based Cyber-Security products & services. The alliance will focus on providing comprehensive cyber-security SOC services to organizations and businesses to combat the aggressively increasing threat vectors and breaches through one-stop hub for comprehensive and custom IT service approach.
This alliance prioritizes on safeguarding business infrastructures with mainly the following features;
Incident Management, Detection & Response
Enhance business’s defence system with multi-step response to remediate threats
Application Security
Choose secure and optimally compliant applications to build safer and robust environments
Cloud Security
Heighten threat responses across cloud network focussing on high priority issues
Digital Identity
Implement centralized single point access, authorization and authentication
Security Risk
Implement smarter decisions reducing uncertainty, mitigating risks and increasing ROI
Threat Operations
Prevent and remediate against sophisticated attacks and reduce exposure to threats
With great pride and tremendous gratitude, we warmly welcome InventOnUs Tech to our strong and diverse family and immensely value this opportunity to serve Cyber Security requirements of businesses in western Maharashtra. With steady expansion in the USA and our recent expansion in the European continent, with this partnership we will strengthen our services to the Indian clients.
To know more about cyber security consultation and SOC services visit InventOnUs Tech Contact us at enquiry@ltssecure.com to know more about alliance and services provided.

LTS Secure and Gemraj technologies Collaboration for Collaboration for Advanced SOAR Based SOC
We are delighted to announce our partnership with Gemraj Technologies Limited, based in Essex, UK; with the collaboration we aim to provide cyber security consultation and serve European market with advanced AI & ML based Cyber-Security products & services. The alliance will focus on providing comprehensive cyber-security SOC services to organizations and businesses to combat the aggressively increasing threat vectors and breaches through one-stop hub for comprehensive and custom IT service approach.
This alliance prioritizes on safeguarding business infrastructures with mainly the following features;
Incident Management, Detection & Response
Enhance business’s defence system with multi-step response to remediate threats
Application Security
Choose secure and optimally compliant applications to build safer and robust environments
Cloud Security
Heighten threat responses across cloud network focussing on high priority issues
Digital Identity
Implement centralized single point access, authorization and authentication
Security Risk
Implement smarter decisions reducing uncertainty, mitigating risks and increasing ROI
Threat Operations
Prevent and remediate against sophisticated attacks and reduce exposure to threats
With great pride and tremendous gratitude, we warmly welcome Gemraj Technologies Limited to our strong and diverse family and immensely value this opportunity to serve Cyber Security requirements of businesses in the UK and European countries. With steady expansion in the USA over the last couple of years, we are very thrilled to expand best of breed Cyber Security Services intercontinentally.
To know more about cyber security consultation and SOC services visit Gemraj Technologies Limited.
Contact us at enquiry@ltssecure.com to know more about alliance and services provided.
Dubai – September,17, 2018 – LTS secure is excited to announce a strategic partnership with Paramount Computer Systems, a cyber-security company from middle-east. The new tie-up will extend a top of the line cyber security mechanism to secure IT infrastructure in the entire Middle East region
“LTS Secure SOC, an intelligent cyber security solution is central to the automated risk management, which brings important cyber security measures to our partner. Our partnership with Paramount Computer Systems Company will allow us to expand the cyber security cover in the new region” – says Satyen Jain, Technology Head LTS Secure.
The new venture will ensure to better management and protection of organizations from advance cyber threats & risks by giving continuous monitoring services through LTS Secure integrated Security Solution SOC based on SOAR (Security Orchestration & Automated Remediation). LTS secure SOC as a service enabled the organization to centrally manage threats and attacks to their information system and data.
LTS Secure director, Satyen Jain says, “Smarter and automated security services strengthen the security measures to fight against cyber-attacks”.
LTS Secure SOC covers the primary dimensions of cyber protection for ventures. The key features of the offering include:
- Continuous Monitoring of all Cyber Infrastructure threats & Vulnerability: Network, Devices, Servers, applications and users from single pane of view.
- Orchestration – Orchestration assists in connecting and integrating of various security application processes together such as alarm management, monitoring network etc.
- Prioritization – As per the criticality of alarms, prioritization in an alarm management is achieved.
- Automation – Automation of severs management is a robust solution to manage a huge amount of logs generated in an organization. LTS SOC is an easy interface to archive and restores the logs in a required time frame.
- Integrated Security Solution – LTS Secure SOC stack has IDAM, CASB, PIM for solving the organization-specific data-intensive problem.
- End to End Compliance Visibility – It provides network path segmentation for fast problem isolation to have real-time analysis and end to end cross-correlation.
The fast-expanding technology infrastructure in the Middle East is vulnerable to continues threat without adequate security cover. Hence it is evident to take proactive measures there is a need to establish a Next Gen SOC platform to secure Middle East Region from cyber-attacks. The partnership with Paramount Computer Systems creates an ideal cyber security measure to negate future cyber threats.
About LTS SECURE
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
To know more about LTS SECURE, contact us at enquiry@ltssecure.com or call us at 800-689-4506 or visit us at https://ltssecure.com.
India, – September, 17, 2018 – LTS secure, a fastest growing cyber security brand announced an acquisition of a new customer in Health care sector. The leading health service provider from Chennai, has joined hands for implementing advanced treat detection cyber security solution.
SIEM, the security orchestration and automated response from LTS secure serves health care industry to provide visibility into Cyber Infrastructure Compliances, identification of security gaps and internal threats.
A combination of advanced analytical tools and correlation engine from LTS Secure, possess threat intelligence and behavior base-lining features, which provide Integrated Security to assist the entire IT layer compliances with broad range of data sources support.
Director of technologies LTS Secure, Satyen Jain says – “Appreciate the evaluation process, that allows a fair chance to vendors to exhibit & prove the capabilities. The customer allowed an equal opportunity to all the vendors to conduct Proof of concept and showcase the results. Great to see that our solution has proven value vis-à-vis other products including leading solutions from Gartner Quadrant”
LTS Secure SIEM a next generation SIEM with “Security orchestration and automated response” covers the primary dimensions of cyber protection for ventures. The key features of the offering include:
- Continuous Monitoring of all Cyber Infrastructure threats & Vulnerability: Network, Devices, Servers, applications and users from single pane of view.
- Orchestration: Orchestration assists in connecting and integrating of various security application processes together such as alarm management, monitoring network etc.
- Prioritization: As per the criticality of alarms, prioritization in an alarm management is achieved.
- Automation: Automation of severs management is a robust solution to manage a huge amount of logs generated in an organization. LTS SOC is an easy interface to archive and restores the logs in a required time frame.
- Integrated Security Solution: LTS Secure SOC stack has IDAM, CASB, PIM for Solving the organization- specific data-intensive problem.
- End to End Compliance Visibility: It provides network path segmentation for fast problem isolation to have real-time analysis and end to end call correlation.
Health care industry deployed LTS SIEM to reduce operation cost, safeguard IT infrastructure, monitor health of critical assets and downtime in IT operations. We are excited to take a charge of health care industry and our clientele with comprehensive cyber security solutions.
About LTS SECURE
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
To know more about LTS SECURE, contact us at enquiry@ltssecure.com or call us at 800-689-4506 or visit us at https://ltssecure.com.
LTS Secure releases latest version 3.5 for automatic threats detection and management.
Los Angeles – August 27, 2018 – LTS Secure, a growing cyber security organization, provides integrated cybersecurity solutions for an IT infrastructure. We have announced the release of version 3.5 of LTS secure. Version 3.5 automatically detects threats across the network and provides a centralized log management system over a dashboard.
IT infrastructure demands to contend cyber-attacks, to accomplish this comprehensive security service, LTS Secure is designed and developed. To overcome the drawbacks of LTS Secure, advanced security LTS Secure version 3.5 is launched. It addresses top challenges experienced by in-house security teams like complexity management of security tools, alarm management, time of response over cybersecurity threats and attacks.
LTS Secure version 3.5 overcomes those challenges through enhanced features.
- Risk scoring – The automatically refreshing dashboard displays assets at highest risk and their updated status.
- Alarm enhancement – With the assistance of artificial intelligence, LTS Secure 3.5 correlates SIME generated alarms with a user.
- Orchestration – Orchestration assists in the alarm management, monitoring network and the asset to reduce the workload.
- UEBA for Office 365 and AWS – UEBA enhances cloud security services, which provides detailed insight of activities happening on cloud platforms.
- Automation of server management – A robust solution to manage a huge amount of logs, possesses an easy interface to archive and restore the logs in a required time frame.
LTS Secure 3.5 directly addresses risks to an IT infrastructure. It provides automatic comprehensive security solution to tackle threat detection and alarm prioritization, which delivers a comprehensive solution to prevent the IT infrastructure.
About LTS SECURE
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
To know more about LTS SECURE, contact us at enquiry@ltssecure.com or call us at 800-689-4506 or visit us at https://ltssecure.com.
LTS Secure director Satyen Jain spoke on 2020 Cyber Security Framework: Orchestration and Prioritization.
Delhi – LTS Secure, the provider of the adaptive SOC platform for cyber security. During the ISACA Delhi chapter June event, the director of LTS Secure Satyen Jain prompted the protection and resilience required in IT infrastructure. He talked about the need for Orchestration and Prioritization in 2020, security stack.
How to protect the cyber network from the advanced cyber attacks like advance malware and different pattern based vulnerabilities? That is the today’s major concern for the IT infrastructure. Considering and understanding the need of the security stack. Satyen focused on the advanced threats, vulnerabilities, and risk of IT Network in the 2020 and what would be the possible ways of detection and prediction?
Satyen majorly focused on the Security big data and machine learning as the network connection establishment is increasing. So the attackers are targeting the cyber network in different ways. He elaborated how to make recent ways of security solution more effective? What would be the best replacement of the security devices or the enhancement in the performance to catch the real time attacks?
The key point of represented at Delhi chapter June event –
Today’s challenges – Represented the current scenario of the challenge like an increase in alarms, noise, and cybercriminals.
Future challenges – In future, the volume of the attack will increase and hence the security measures have too.
Advance attack – The multi-vector attacks which penetrate an organization on multiple levels.
2020 security framework – It contains the strategy of creating the awareness, orchestration, continuous monitoring and response, prioritization and automation.
Machine learning and AI – Elaborated, how the machine learning and AI are used for the orchestration and prioritization of the threat to enhance the security measures?
The cybercrime motivates LTS Secure to invest in the innovation of the security stack that would provide the most effect and protective security stack.
ABOUT LTS SECURE :
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
To know more about LTS SECURE, contact us at enquiry@ltssecure.com or call us at 800-689-4506 or visit us at https://ltssecure.com.
Modernization of the IT infrastructure for the optimization of the business comes with a security concern. In any organization, the various IT infrastructure security solutions and preventive measures are used to protect it from the enormous cyber-attacks.
There are various preventive measures and tools are available like antivirus, firewall, DLP (Data Loss Prevention), used to detect the threats, malware and vulnerabilities. Till the time, the enterprises are taking help of these preventive measures and they are effective. However, they don’t give a composite and profound solution as they work best as an individual system. For the business, there is need of comprehensive threats resolution solution within the desired timeline.
Today most of detection and protection security solutions are working in the Silos and whenever any flow or suspicious activity occurs, the alarms or alerts are generated separately with the own priorities. Bombardment of alarms and alerts form all these security measures become challenging and unmanageable to the IT operation team and reducing their effectiveness, which is leading to unattended priority security alarms.
To protect the IT infrastructure the IT operation team has to go through the each and every alarm and alerts, as per the criticality need to shortlist and prioritize them. The increased count from the various security solutions causes the delay in the response time of IT operation team. At the peak time of operation, it becomes difficult task to prioritize them and work out for a solution. This causes loss of time and ineffectiveness of the resolution as time false and real threat remains open for longer time.
As such out of these alarms, many are simply making noise, which needed to be discarded on the real time, so IT operation team can take immediate action on actual threats. Machine learning and knowing context of the alarm would help in alarm suppression decision.
To automatically suppress the noise and prioritization of real alarms, there is need for the centralized and intelligent alarm orchestration and prioritization solution. This solution should be able to analyze the alarms in a real time and helps to manage the execution of them as per the criticality based on security context. To accomplish this task the centralized alarm solution must be able to collect all the alerts and alarms from the entire protection and detection security solutions irrespective of their alarm format and location. The Solution should able to discard the noise and prioritize them according to the impact of the alarm and keep considering of the user and business context. To bring context, there is need for Identity and Access Management solution integration.
Once the orchestration and prioritization of the alarm are accomplished the enterprise has to look at the strategy of to automate response to reduce the response time and make IT operation time efficient.
To overcome these challenges, LTS Secure came with the solution based on Security Orchestration, Automation and Response. LTS Secure Integrated Security Solution is based on SOAR (Security Orchestration, Automation and Response) Stack. It has the capability of collecting the alarms from all IT layers and security solutions to orchestrate and prioritize alarms in real time. Solutions are not only prioritized based on RISK and Asset Values, but it brings context from inbuilt Identity & Access Management and Access Broker modules. IT has the capability to collect and monitor alarms of cloud Infrastructure and applications.
Orchestration feature of the solution decides based on knowledge gathering from integrated security solutions, machine learning and context of the alarm to discard noise and automate real threats
LTS Secure Integrated Solution is the next generation Solution for SOAR Stack. It makes security team effective and efficient by making them capable to take action in short span of time even though the continuous alarms and threats are coming in the industry.
ABOUT LTS SECURE:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
To know more about LTS SECURE, contact us at enquiry@ltssecure.com or call us at 800-689-4506 or visit us at https://ltssecure.com.
LTS secure is the intelligence driven security operation center platform and one of the organizers of the Tie Global Summit || 2018. Once in the year, the event is organized for the entrepreneurs across the globe. LTS secure exhibited the their Security Solution based on SOAR (Security Orchestration, Automation, and Response) stack which is designed to detect, prevent frauds, and data leaks from the internal and external attacks on the cyber infrastructure.
LTS Secure SOAR stack is Continuous monitoring of cyber threats and vulnerabilities of the IT infrastructure; nowadays ISV is highly demanding the LTS secure SOAR stack to get the cyber security.
Chief Minister of Maharashtra Shri Devendra Fadnavis and Bollywood superstars visited exhibited stalls.
ABOUT LTS SECURE:
LTS Secure is an Integrated Security Platform (SIEM + UEBA + CASB + IDM) that enables continuous monitoring & detection of Threats, Vulnerabilities and Risk of IT Network, Applications and by Users in a single pane based on Security Orchestration, Automation and Response.
To know more about LTS SECURE, contact us at enquiry@ltssecure.com or call us at 800-689-4506 or visit us at https://ltssecure.com.