Introduction of Firewall in Computer Network
UEBA (User & Entity Behavior Analytics) is the most promising solution to fight against cyber threats and fraud as it allows us to get ahead of the attackers by detecting risks and restrict them. Know the Introduction of Firewalls in Computer Network It is the best network security device and assists users block malicious software from accessing the Internet on affected computers.
UEBA successfully detects malicious and abusive activity that otherwise goes unnoticed, and effectively consolidates and prioritizes security alerts sent from other systems. Organizations need to develop or acquire statistical analysis and machine learning capabilities to incorporate into their security monitoring platforms or services. Rule-based detection technology alone is unable to keep pace with the increasingly complex demands of threat and breach detection.
UEBA to provide insights on cyber security and analytics. Our solution analyses volumes of data to establish a baseline of normal user and system behavior, and flag suspicious behavior anomalies. The result is a sophisticated artificial intelligence platform that detects insider and cyber threats in real time.
Advantages of UEBA
- Provides behavior based analytics for detecting insider and targeted cyber attacks.
- User centric monitoring across hosts, network and applications
- Privileged account monitoring and misuse detection
- Provides huge reduction in security events warranting investigations
Use Cases
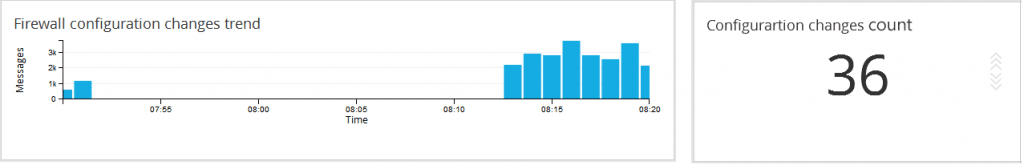
a. Firewall configuration analytics
Keep an eye on the changes being made to the network security infrastructure. Administrators may make some intentional or unintentional error or carry out an improper change while acting on a firewall configuration change request giving room for breaches. This Firewall Change Management report precisely helps in detecting such events. It helps find out ‘who’ made ‘what’ changes, ‘when’ and ‘why’. Not only that, it alerts you in real-time on your mobile phone when changes happen.
The Firewall change management can generates alerts for the Firewall device configuration changes in real-time and it notifies via Email, HTTP alerts.
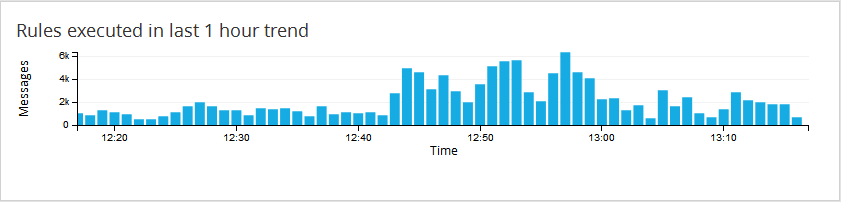
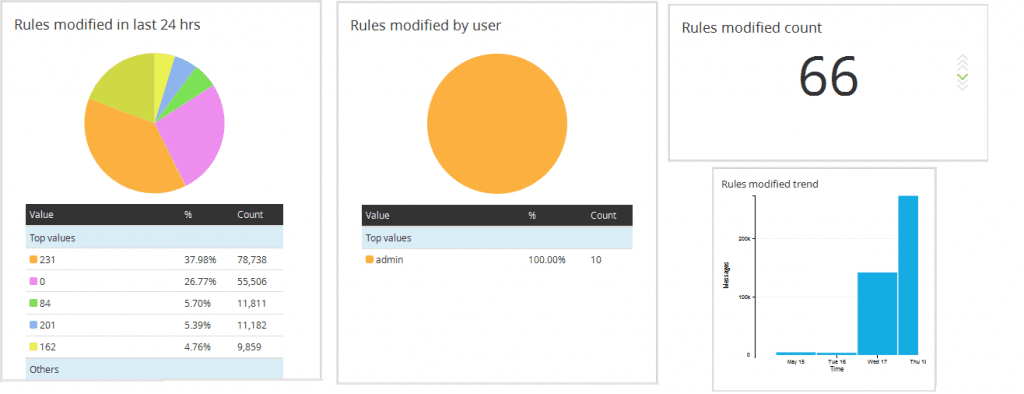
b. Rules created / modified in a particular time span
Administrator creates lot of rules on need basis and forgets to remove them if not required. After a certain period of time, we will be having a huge set of rules in firewall which may not be even executing for a long period time. This report would help to find such rules which can be removed from the system and can help the administrator to manage the system more efficiently.
C. Rules not executed in a particular time span
Administrator creates lot of rules on need basis and forgets to remove them if not required. After a certain period of time, we will be having a huge set of rules in firewall which may not be even executing for a long period time. This report would help to find such rules which can be removed from the system and can help the administrator to manage the system more efficiently.
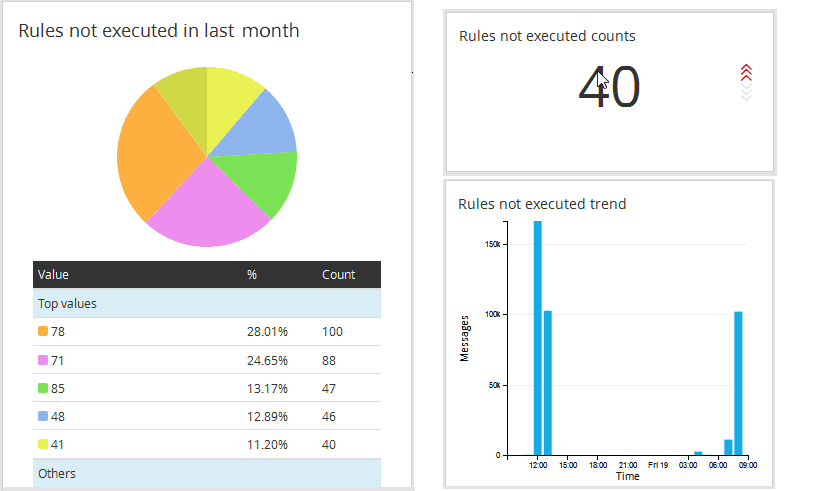
Visibility
The system provides trend of events happening over a period of time which would help the system analyst to understand the behavior of such events and can predict the trends of such occurrences. This would prove very helpful in finding or investigating critical system issues.