LTS SECURE SOC AS A SERVICE
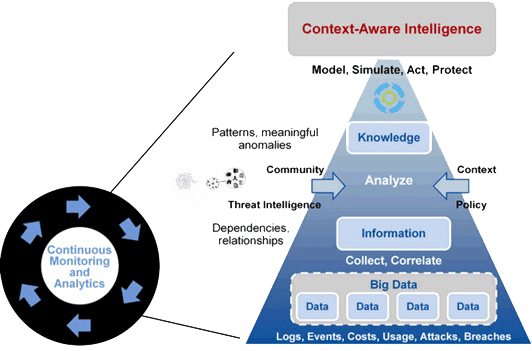
LTS Secure Intelligence Driven SOC Provider is a Cloud based Security integrated Context-aware Security protection platform and that provides and integrates prediction, prevention, detection and response capabilities by leveraging adaptive security framework. LTS Secure comprehensive SOC as a service provides continuous monitoring for all layers of the IT stack: network packets, flows, OS activities, content, identities, user behaviors and application transactions for protection from advanced threats using integrated Adaptive Security framework.
We move enterprise from “incident response” to “continuous response”, by supporting network security monitoring 24 * 7 of all layers events, activities and transactions and continuous threat protection process.
LTS Secure Intelligence Driven Security Operation Center Cloud based Security SOC Provider delivers continuous network security monitoring of all IT layers, Enable Controls Management on Identities i.e., Privilege or User with in-depth visibility of user behavior, advance threats, risks and compliance dashboards. Our SOC as a service Analytics, works based on, patent pending pattern recognition algorithm and correlation engine to correlate Device, Activity, Identity and Context together.
FEATURES
![]()
Real Time Threat Intelligence
Tons of threats monitored worldwide & Ingested to LTS Secure SIEM as Live Pulses, so your SOC has latest updated intelligence for stopping newest of breaches.
![]()
User Entity Behavior Analytics
To be able to detect new wave of advanced threats we need advanced UEBA platform driven alerting which can do PIM (Privileged Identity Monitoring) and correlate any security events from Cloud apps or On-premise applications/Users to give you full visibility from single pane of management.
![]()
SOC Automation & Orchestration
LTS Secure SOAR Suite Combines Automation, Orchestration, & Big-Data powered investigation into a single & comprehensive incident response platform that triples SOC efficiency, provides unprecedented visibility & reduces time-to-respond.
![]()
Enhanced Correlation Engine
LTS Secure SIEM has enhanced correlation engine, which learns from past events, keep a database and presents Alarms for APT.
![]()
IT Risk And Compliance Reporting
Full-fledged VA capability coupled with predefined compliance reports provide you freedom from manual reviewing of the compliances at the same time reducing your Overall IT Spend, So You Can Comply Duly With The Regulatory Standards, be it ISO 27001, PCI-DSS, HIPAA, SOX, Etc.
![]()
Cloud-Based Environments Security
Eliminate Blind spots, Detect Emerging Threats, Respond Quickly & Enhance Your Current Security Investments.
BENEFITS
![]()
Advance Threat Detection
Advance threat detection for all data on End-points/ Databases (MySQL, MSSql etc.), Intranet/ Internet Users, Apps On Prem/ Cloud & Network-devices like Routers, Switches, NGFW, DLPs & EPMs.
![]()
Integrated Security
Modular Network, User & Application Visibility from single-solution. On-prem & cloud monitoring alarms prioritization saves 50% of cost & provides a faster ROI.
![]()
Orchestration & Automation
Reduce false positives with orchestration rules. Reduction In False Positives by 45% & Increase of automation by 60%.
Compliance reporting & gaps analysis to reduce audit time & audit report submissions.
![]()
Asset-Based Risk & Compliance
Consolidation of threats & vulnerabilities with user & business context. Reduce business continuity risk by 73%.
SOC CAPABILITIES
- Geographical Redundancy built in with operations in India and USA.
- 24x7x365 Security Operations Coverage
- Staff includes analysts, engineers, and management working together in accomplishing our Sercurity Objectives and Deliverables.
- Fully trained on entire suite of Security products.
- Regular investment in training and growing our technical staff.
- Mature processes and controls based on industry accepted frameworks (NIST Cybersecurity, ITIL Service Management, and GAMP)
- Team of Senior Security Analyst and Resources with in-depth knowledge of security, compliance, and operations
- Clear documentation of the categories, events, process, escalation and expectation of the service before the engagement is started with continuous improvements
- Real-time updated database for Vulnerabilities/Threats globally
- Proven processes and support to delivery security to clients
- Over 20 years experience in delivering Managed Services.
- A “Customer First” culture!

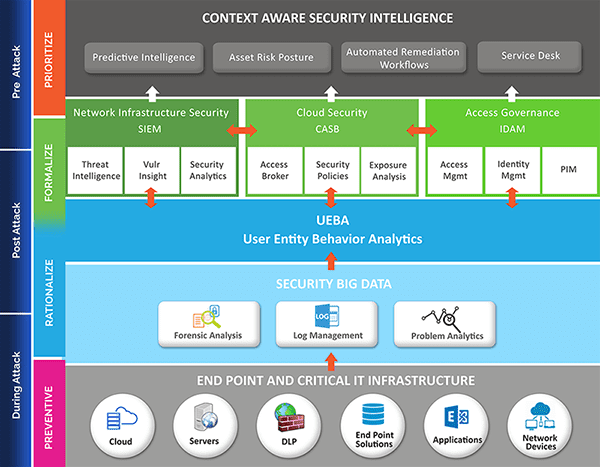
LTS SECURE’S INTELLIGENCE DRIVEN SOC STACKS CONTAINS
Security Big Data
Solve organization-specific data intensive problems; collect and analyze diverse data types at high volume.
- Forensic Analysis
- Log Management
- Problem Analytics
SIEM
Adaptive SIEM monitors all logs from devices on the network like servers, firewalls, routers, switches raising continuous alerts for threats and risks.
Read More >
Access Governance
Access Governance is a combined model of process and technology to manage and secure access for the enterprise resources/applications. It plays a key role in developing security infrastructure.
Read More >
CASB
CASB does the User Behavior Analytics based on user activity raising anomalous alerts resulting in protection of data and applications in real-time.
Read More >
Security Analytics
Advanced analytics around user behavior and other entities, such as End-points, networks and applications.
Read More >
PIM
PIM does Privilege account management and monitoring ensuring a protected, controlled and compliant environment.