Know best Zero Trust Security
Changing from ‘Trust but Verify’ To ‘Always Verify, Never Trust’
NEVER TRUST.
ALWAYS VERIFY.
Overview
With remote users connecting via unmanaged devices to critical servers, sensitive data and business applications over the internet, organizations are in need of a new security model that is capable enough to adapt to the complexities brought on by the modern enterprise & remote workforce and is able to protect apps, data, users & devices.
LTS Secure’s Zero Trust Model ensures that all of our users, regardless of their location, have to be authenticated, authorized, and continuously validated against defined security configuration before they are granted access to applications and data.
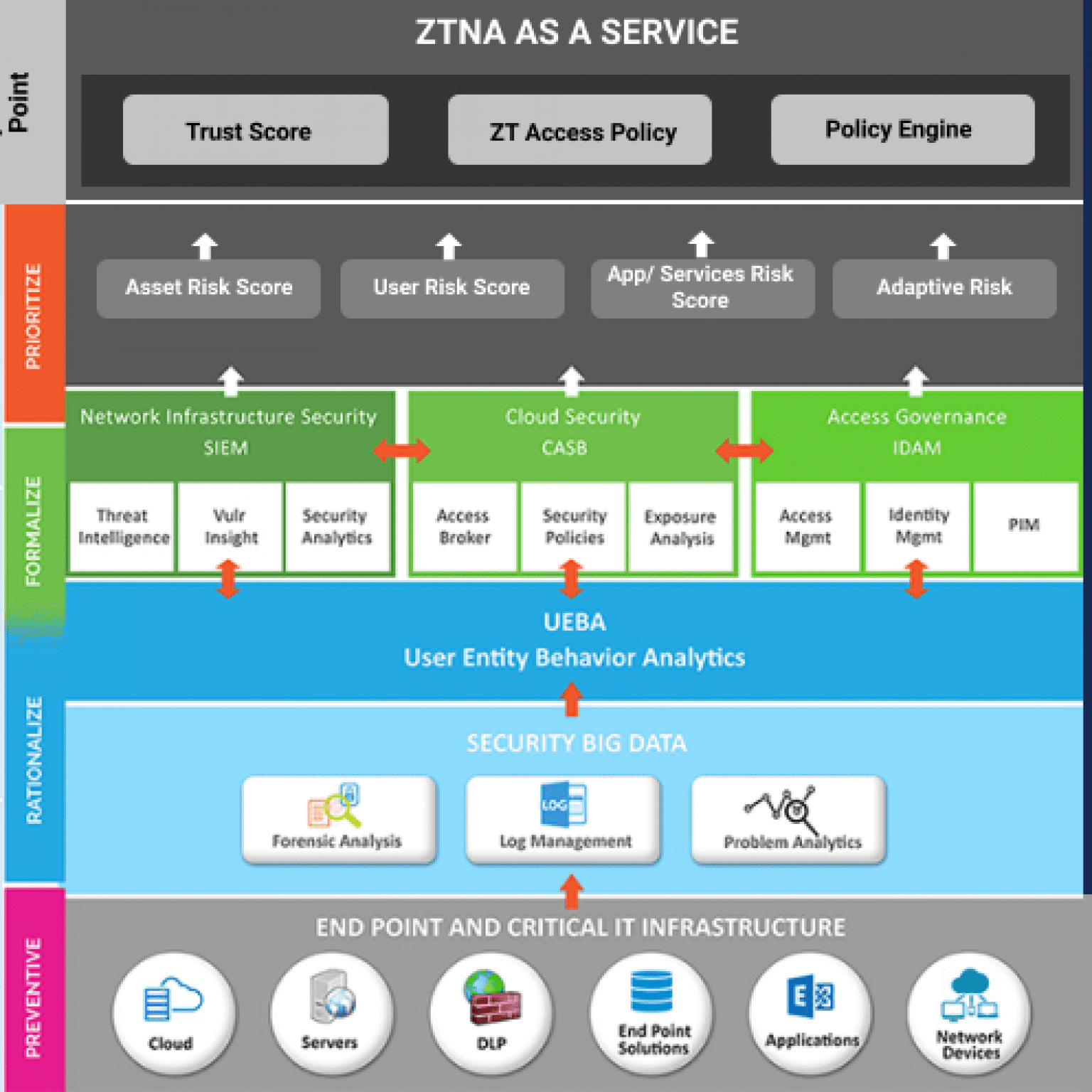
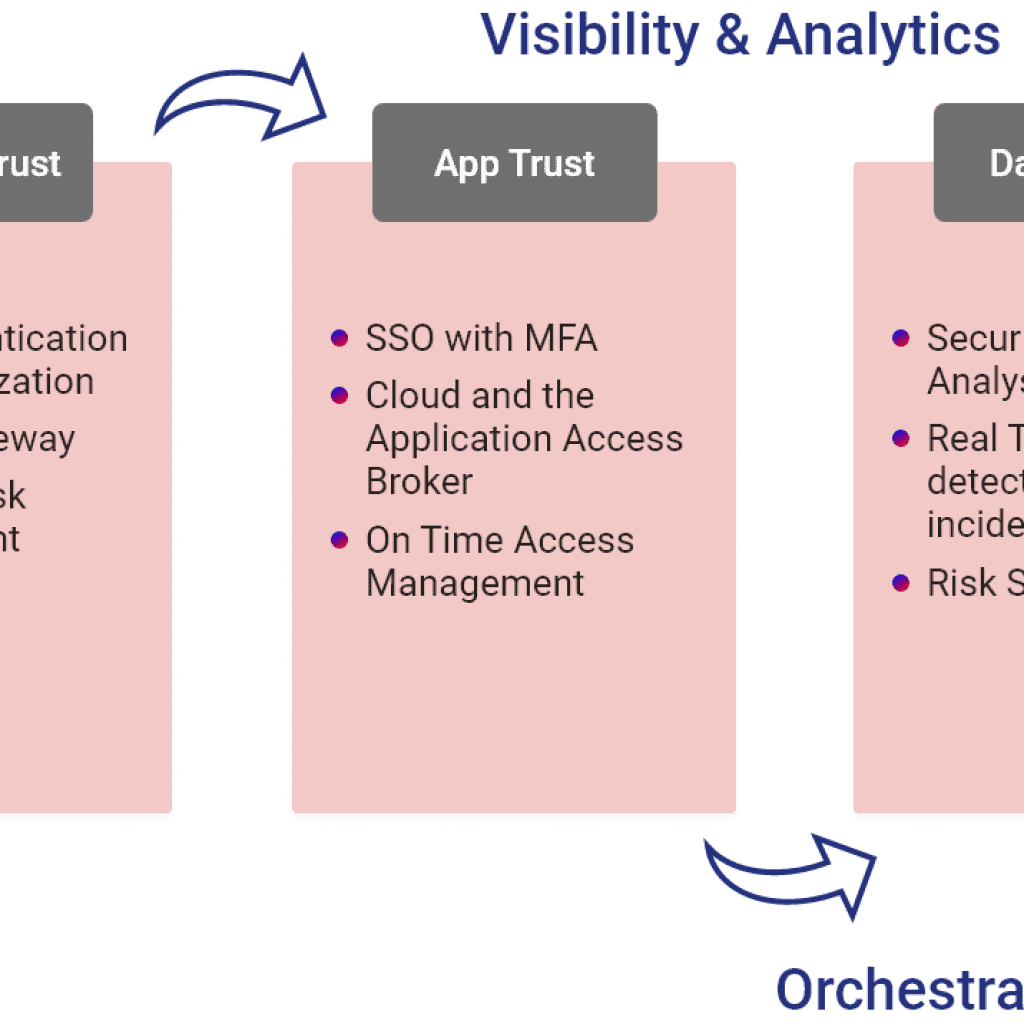
Key Benefits
Uniform Security
Enforce your complete security mechanism across entire infrastructure.
Risk Mitigation
Reduce security gaps and lower the risk of lateral movement.
Increased Visibility
Centralized logging for inside to detect patterns of unusual/ suspicious behavior.
Remote Access
Allow your employees to work more securely from anywhere.
Secured Cloud Environment
Enforce stringent security controls to your cloud environment.
Let's Connect Now !


