Overview
LTS Secure Identity Management allows you to comprehensively and securely manage the complete identity life cycle of users, devices, and things. From identity to device registration, provisioning, synchronization, reconciliation, and more, your users and customers can feel safe as they move between devices and service.
Along with LTS Secure Privileged Access Management, LTS Secure IDM solutions has the potential to provide greater access to organizations, which can drive productivity, satisfaction and, ultimately, revenue. At the same time, it keeps a record of the identity of every individual in order track his activity and check who is misusing his/her access related privileges.
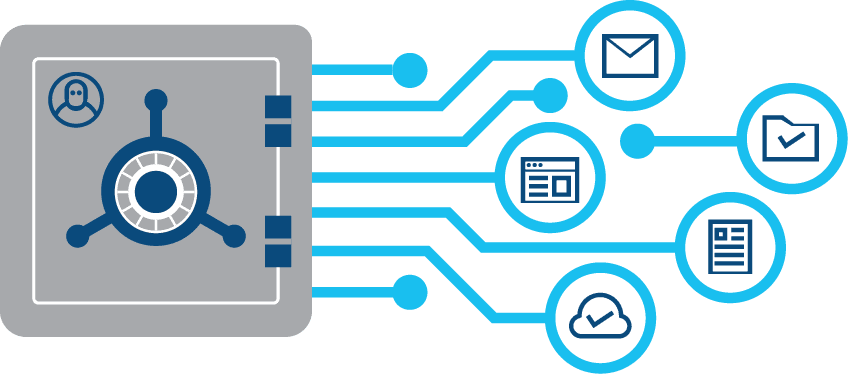
Ensure that all cloud apps, On Premise Applications, IoT Devices and on Mobile leverage a single identity store. LTS Secure Privileged Identity Management is an administrative area that deals with identifying individuals in a system (an enterprise) and controlling their access to resources within that system by associating user rights and restrictions with the established identity.
LTS Secure Identity Management allows you to comprehensively and securely manage the complete identity life cycle of users, devices, and things. From identity to device registration, provisioning, synchronization, reconciliation, and more, your users and customers can feel safe as they move between devices and service. Along with LTS Secure, IDM solutions access management, LTS Secure Identify Management has the potential to provide greater access to organizations, which can drive productivity, satisfaction and, ultimately, revenue. At the same time, it keeps a record of the identity of every individual in order track his activity and check who is misusing his/her access related privileges.
Key Features
Role-based Provisioning
Create and manage roles assigned to users based on organizational need and structure such as job function, title, geo, etc.
REST API
Pluggable server-side scripting engine provides Javascript and product-wide Groovy support out of the box for extensibility and customization.
Flexible Data Model
Supports choice of data model to meet the needs of your deployment – either a data full model for current data or data sparse model for faster access.
Password Management
Ensure consistency across all applications and data stores, such as Active Directory and HR systems.
Cloud SaaS Connectors
• Simplifies connectivity to cloud-based SaaS resources such as Salesforce, Microsoft and Google Apps with out-of-the-box connectors.
• Centralized management of identity data across resources guarantees consistency with ability to synchronize and reconcile bi-directionally, on-demand or as a scheduled update.
Synchronization and Reconciliation
• Synchronization delivery guarantees enable roll-back if one or more remote systems are unavailable, for both on-demand and scheduled resource comparisons.
• Reconciliation discovers new, changed, deleted, or orphaned accounts to determine user access privileges to detect and synchronize changes to accounts, entitlements, and passwords, and perform user access remediation tasks.
Data Model Visualization
Visualize identity relationships through the LTS Secure Identity Management, management console. Plus build customized dashboards, integrated with Kibana, that include bar, line, scatter plots, and pie charts that give shape to the data that LTS Secure Identity Management is handling.
Shared
Services
The Common Audit Framework provides a means to log data consistently across the LTS Secure Identity Platform™, and enables you to correlate events and transactions. Audit topics, such as access and activity, can be configured independently delivering the data you want to the appropriate business services. Includes handlers for CSV files, JDBC connections, Syslog, JMS, and Elasticsearch (part of the ELK stack).
Self-Service & Profile Management
• User self-service significantly reduces help desk costs and increases user productivity by automating password reset and ensuring compliance with a secure, centralized password policy.
• Allows end-users to create and manage profiles, configure privacy setting, and give consent for data-sharing.
Social Registration & Authentication
Accelerates registration and login by using any social IDP that supports OpenID Connect or OAuth 2.0 such as Facebook, Google, and LinkedIn to gain insight and build common user profiles for a centralized single view of the customer.
Workflow Engine
Provides workflow-driven provisioning activities, whether for self-service actions such as requests for access or for admin actions such as updating entitlements, on/off boarding, bulk sunrise or sunset enrolments, handling approvals with escalations, or performing maintenance. The embedded Activity engine supports BPMN 2.0 for standards based business focused management.
OpenICF Connector Framework
Leverages the new OpenICF 1.5 framework (Open Source Identity Connector Framework) for resource connector development, including amongst others, a PowerShell Connector, a Generic Scripted Connector that allows for integration with anything that Groovy supports; REST, SOAP, JDBC, JSON etc.
Key Benefits
Eliminate Weak Passwords
Enforce best credential management practices and eliminate the risks posed by weak and default user passwords .
Detect Insider Threats
Limit damages caused by breaches by implementing strict access policies depending of role of users in a company .
Track Anomalies
Transform traditional credential management by implementing various advanced technologies and strategies like AI, ML, risk-based authentication etc.
Multi-Factor
Ensure highly secure environment with two-factor, three factor and multi=factor authentication with added steps like fingerprint and iris scanning and face recognition.
Let's Connect Now !
