Overview
What is User Entity Behavior Analytics (UEBA)?
User and Entity Behavior Analytics (UEBA) or User Behavior Analytics (UBA) is a cyber security tool that detects threats by identifying activity that deviates from normal baselines. A kind of solution or feature. UEBA can be used for various reasons, but the most common uses are to monitor and detect unusual traffic patterns, unauthorized data access and movement, and suspicious or malicious activity on computer networks or endpoints. A CASB solution should have greater visibility into user activity across all SaaS applications that users access.
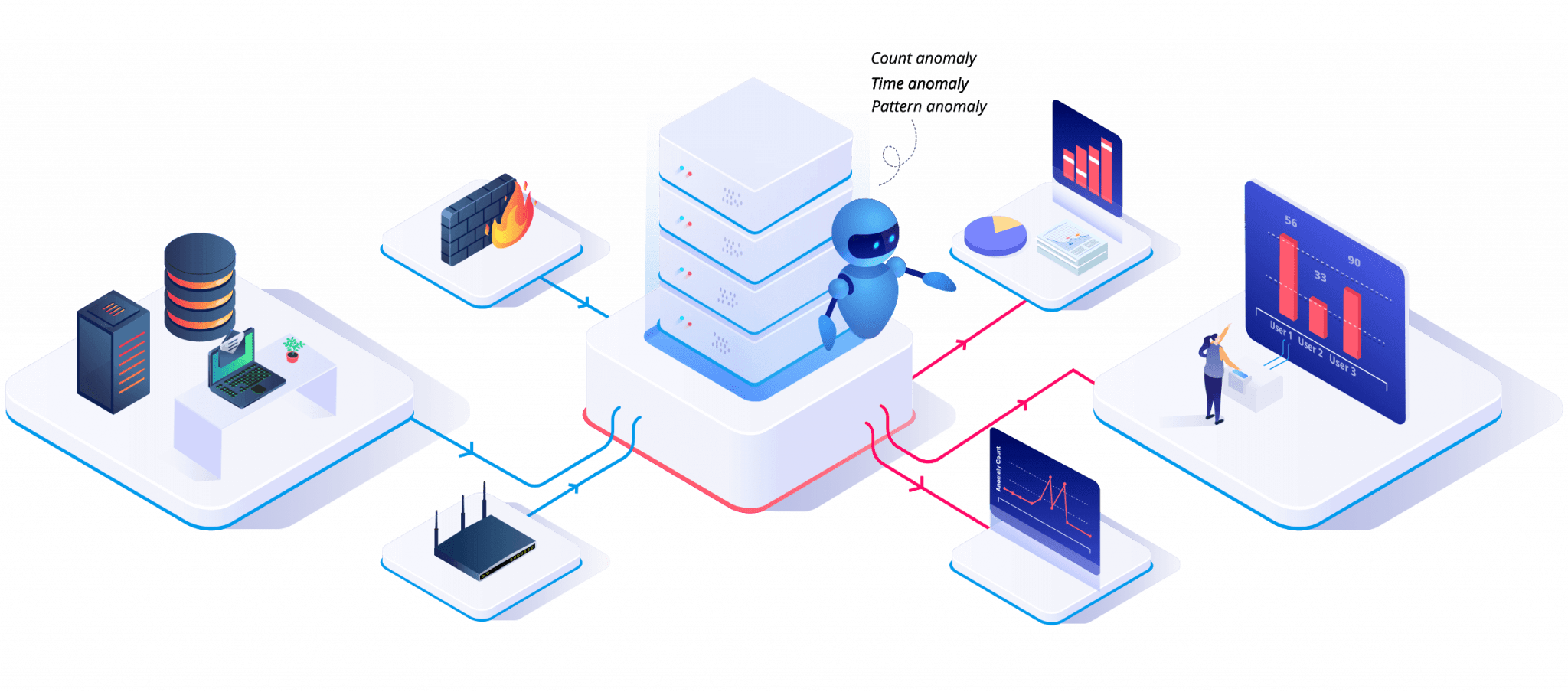
Why Would an Organization Need UEBA?
Security operations often use SIEM (Information and Event Management) platforms to monitor and identify potential security threats. SIEMs gather event logs and security alerts but struggle to detect unknown or advanced security threats that don’t involve malware. Credential theft — or an internal or external attacker who has previously had access to your network.
How Does UEBA Work?
To be effective, You must install a UEBA Solution on every device used or connected by every employee in your organization. This includes company-owned as well as employee-owned devices. Devices used part-time can also be targeted by cyber-attacks. Many companies ask their employees to install their UEBA on their routers, which can serve as an attack vector. Connecting to a corporate network through a home router opens up even more possibilities for cyber-attacks.
The UEBA Solution Has Three Main Components -
Analytics collects and organizes data it determines to behave well from users and entities. The system creates a profile of how each type behaves regarding application usage, communication and download activity, and network connectivity. A statistical model is then formulated and applied to detect anomalous behavior.
As your business grows and evolves, integration with other security products and systems is essential. Most have security stacks, including legacy systems that may not keep up with today’s ever-evolving threat landscape. When properly integrated, the UEBA system can compare data collected from various sources, including logs, packet capture data, and other datasets, and integrate them to make the system more robust.
.Presentation is the process of communicating the results of the UEBA system and creating an appropriate response. Some UEBA systems create an alert for the employee or IT administrator and suggest further investigation. His other UEBA systems are set up to respond immediately to suspected cyber-attacks by automatically shutting down that employee’s network connection.
Benefits of UEBA -
The rise of UEBA is fueled by the fact that traditional security products such as web gateways, firewalls, intrusion detection and prevention tools, and encryption products such as virtual private networks (VPNs) can no longer protect organizations. An experienced cyber attacker finds a way to infiltrate a system one way or another. It is essential to detect even the seemingly most minor anomaly.
Social engineering and phishing are also increasing at an alarming rate. These tactics attack employees rather than an organization’s hardware, forcing them to click links, download software, and send passwords. Infecting a computer is a potentially large-scale cyber-attack. UEBA tries to detect even the slightest abnormal behavior and prevent small-scale phishing schemes from turning into large-scale data breaches.
Some Essential Benefits of UEBA and Why Enterprises Should Consider Adopting It –
Requires Fewer IT Analysts
As with all corporation software that leverages gadget learning and synthetic intelligence, software program replaces the time and effort of employees who might typically be doing the process. This prospect may excite many organizations —while IT experts would possibly drawback—however, the development of UEBA answers will not result in a dramatic headcount discount.
Suppose a company requires fewer IT Syslog analysts once the UEBA system is on autopilot. In that case, it can divert those staff members to other higher-value projects that might be more mission-critical.
Larger businesses with complicated safety necessities, including multinational corporations and governments, understand the need for additional IT staff and protection analysts to set up, configure, and manage the machine and communicate regularly with employees. Moreover, suppose the agency decides against incorporating automatic reaction competencies, which prefer to analyze the uncommon behavior earlier than taking motion as an alternative. In that case, you will dispatch additional safety analysts to the worker or hardware place.
Reduced Costs -
Continuing with the previous point, reducing the number of analysts an organization needs to perform the UEBA system’s work reduces IT expenditures. However, as mentioned earlier, this does not mean you should lay off the entire security analyst staff once the system is up and running. Machine learning still requires human intervention in any environment.
Additionally, proactively stopping ransomware attacks can be considered cost savings. UEBA prevented companies from paying cyber attackers to restore their systems or losing money in hours or days of lost productivity due to servers being rendered unusable by malware attacks.
Risk Mitigation-
That is the primary benefit of the UEBA system. Precautions in the form of isolated security products only go so far. Enterprises today face a growing array of threats that are becoming increasingly difficult to defend against as the number of devices and locations proliferates. When offices are closed, employees can work from home by connecting multiple devices to their routers and accessing the public internet.
The cybersecurity solution can not only be downloaded to an employee’s home device but also the IoT and rugged devices deployed in various environments such as retailers, warehouses, and hospitals. Any device connected to a corporate network can be vulnerable to cyberattacks. It’s impossible to track every device IT teams use physically; UEBA does much of the work for them regardless of size.
UEBA can be used not only for threat detection but also for regulatory compliance. Regulated industries, which include financial offerings and healthcare, have security requirements that companies should comply with. Simple, routine network monitoring tools can determine if your software has been updated with the latest security patches, but UEBA goes one step further. A Cyber Risk Assessment helps an organization understand, control, and mitigate all forms of cyber risk. This is a critical component of our risk management strategy and our approach to privacy.
Cyber security solutions are technology tools and services that protect your business from cyber-attacks that can lead to application downtime, theft of sensitive data, reputational damage, fines, and other negative consequences. Detecting anomalies can help IT staff determine, for example, that a router is not configured with industry-standard, most robust security settings. This allows the team to address the situation immediately and saves the company from paying fines or going to court for violations.
The UEBA system has several drawbacks. One is the price. . It can be out of reach for some enterprises.
productivity due to servers being rendered unusable by malware attacks.
Key Features
Data
Integration
Easily compile data from event logs deep packet inspection, and outside threat intelligence, attribute behaviours and create master database containing all communications within the network to establish baseline. Use this baseline to later pinpoint deviations indicating malicious intent.
ML Enabled
Analytics
With Machine learning abilities to enable user and entity behaviors modelling and analytics based on various organizational components. With real time security events and ML, detect and prevent threats that traditional tools miss.
Reduce False
Positives
Building profiles for each entity, UEBA uses context surrounding behaviors to differentiate between attacks and false positives.
Key Benefits
Detection of Hijacked Accounts
Attackers who steal valid user credentials behave differently than real users. UEBA uses real-time detection to ascertain if something is out of norm and responds to the threat through various real-time responses such as Block, Modify, Re-authenticate or Multi-factor authentication. This ensures that the real threats are getting addressed before they try to harm the system.
Reduced Attack Surface
UEBA sends insights to the users and the security teams through interactive analytics which allows them to know about the loopholes or weak points before an incident happens. These insights help reduce the attack surface which makes it difficult for the cyber attacker to breach the network.
Privilege Abuse and Misuse
In any organization the privileged users have extensive access to the system, data and applications which is why they present a higher risk to the organization. UEBA’s algorithms ensure that the access rights are used appropriately and give an overview of what kind of privileges individual users should have.
Improved Operational Efficiency
It takes a lot of efforts to identify threats manually through alerts. UEBA can manually identify and validate threat without manual intervention through automation and security intelligence. This level of automation allows security to focus on real threats rather than alert chasing.
Data Exfiltration Detection
UEBA analytics help to detects potential data exfiltration before
it happens, thus allowing businesses time to prepare a strategic
plan to prevent data theft. It can even help identify Advanced
Persistent Threats (APT).
UEBA has proved itself to be an
indispensable asset in the world of cyber security. According
to experts user and entity behavior analytics is a better model
for attack detection and maintain that it is going to enable more
accurate detection of cyber attackers threatening networks.
Let's Connect Now !
