Benefits Of Automation SOC
Decrease Time from Threat Detection to Importance of Automation in SOC
SOC, or Security Operation Centers, are gaining traction in various businesses across a wide range of industries. Several large to small businesses have already begun to implement SOC, while others are either establishing their own or partnering with an MSSP (Managed Security Service Provider). In all circumstances, the SOC function combines and unifies the incident detection, containment, eradication, and recovery processes, monitoring, vulnerability management, advanced security monitoring, compliance monitoring, and a variety of other critical activities. Overall adoption of these terms and technologies has the wider-spread scope of SOC Automation for modernizing the environment.
Is SOC Automation Necessary?
Is it possible to analyze all incidents in real-time with hundreds of thousands of alerts, events, and logs flooding the security monitoring system? As a result, the go-to answer is “SOC Automation,” which is the only method for a business to handle the growing demand for the effectiveness of their most vital IT Security function. However, relying solely on automation is not the best option. A device or an application that operates according to rules and norms cannot replace the human intellect element.
A certain level of automation is one of the most critical aspects of security operations. Incorporating automation into SOC activities and a redesigned process that evaluates outputs with human intellect should result in a good balance and a dependable IT security function within the company. SOC Automation allows defining, modifying, or redefining the runbook or playbook’s rules, with people leveraging and overseeing the process.
SOC Automation: The Key To A Smarter SOC
The problem with a continuous focus on adding detection tools is that we have an excess of warnings that traditional SOCs can’t handle. However, enterprises can scale operations with SOC Automation to keep pace with the wave of data generated by advanced detection tools.
Rather than keeping up with the growing number of security alerts by hiring more analysts, security automation services allow SOCs to scale in several important ways.
1. Advanced Threat Detection
Quick and early identification of a threat is a critical step in the security lifecycle, especially when threat actors are learning how to breach enterprises at an alarming rate. However, the complexity of multi-stage, covert attacks is making detection difficult. Advanced threat detection is a typical solution that employs correlation rules, context enrichment, entity analytics, and other detection content to detect threats.
SOC Automation uses behavioral observations, real-time intelligence, and context to identify suspicious activity. A high-power cybersecurity analytics solution collects, correlates, and analyzes all security-relevant data focusing on automated enrichment that helps improve the signal, reduce noise, and detect the threats that matter most to the business.
A practitioner typically supports the use of modern tools- defined alerting framework, an approachable AI, and ML for intelligent risk prioritization and categorization.
2. Integrated Security
Integration and orchestration without automation won’t help enterprises get the most out of their investments in detection and response. A Cyber Analyst’s first task is to add context to an alert through enrichment. For example, resolving an IP address to a device, detecting what system the device belongs to, and assessing if the system or other observables have any known vulnerabilities.
The first step in SOC Automation is enriching the alerts automatically so that companies can prioritize the reaction and eliminate false positives rather than working with an extensive list of unrelated warnings. For example, an analyst must respond to an attack on a privileged user differently than a non-privileged user with limited access in case of urgency.
Integrated security automatically adds context to an alert, so those alerts are prioritized and potentially correlated as a single incident and changed together as a potential attack scenario.
3. Orchestration & Automation
Although the high volume of alerts generated by prevention and detection tools can be a blessing and a curse for SOC teams, these alerts indicate that your tools effectively monitor and block threats as they approach your network. But the reality is that high volumes of alerts lead to false positives that may diminish the effectiveness of the cyber security tools, directing the security analysts’ attention in the wrong direction.
When the SOC team is overwhelmed by alerts, false positives become a regular occurrence that helps attackers gain a foothold into your network quickly without being detected. Therefore, a company takes 197 days to detect a data breach.
SOC Automation & orchestration reduces false positives with orchestration rules. They focus on assembling the alerts into the probability of different types of attacks that help 45% of reduction in false positives and increase automation by 60%. It also enables enterprises in compliance reporting & gaps analysis to reduce audit time & audit report submissions.
4. Asset-Based Risk & Compliance
Even though cybersecurity spending is expected to increase by more than $1 trillion by 2022, attackers continue to evade through the enterprise network. The problem is that traditional SOC are limited to reactive monitoring without acknowledging that a response is needed. When alerts are triggered, traditional SOC response is slow, and the damage is magnified and more complex to resolve.
To be proactive, enterprises must assemble multiple alerts into the probability of an attack scenario. Since there are various steps that an attacker takes to implement a complex attack, asset-based risk and compliance consolidate all the threats and vulnerabilities to reduce business continuity risk by 73%.
With SOC Automation, enterprises can keep ahead of the latest cyber security threats and go beyond leveling the playing field to being in another league altogether.
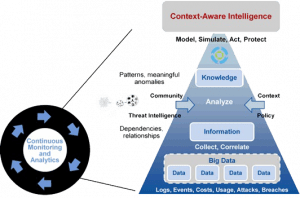
LTS Secure is a SOC Provider that provides and integrates prediction, prevention, detection, and response capabilities by leveraging an adaptive security framework. We move an enterprise from “incident response” to “continuous response” by supporting network security monitoring 24 * 7 of all layers of events, activities, transactions, and a continuous threat protection process.
Our SOC Automation analytics works based on a patent pending pattern recognition algorithm and correlation engine to correlate Device, Activity, Identity, and Context.
Connect to Consult with LTS Secure Team to explore to leverage one of a kind SOC platform as-a-Service (SOC PaaS) and take a holistic approach in implementing innovative strategies that will provide a cohesive protection to your customers.